On Friday, a hacker took down a huge chunk of the dark web. Visitors to over 10,000 Tor hidden services running on Freedom Hosting II—a hosting provider for dark web sites—were greeted with a perhaps surprising message, The Verge reported.
“Hello, Freedom Hosting II, you have been hacked,” the message read. According to a report from independent security researcher Sarah Jamie Lewis, Freedom Hosting II ran around 20 percent of all dark web sites.
Videos by VICE
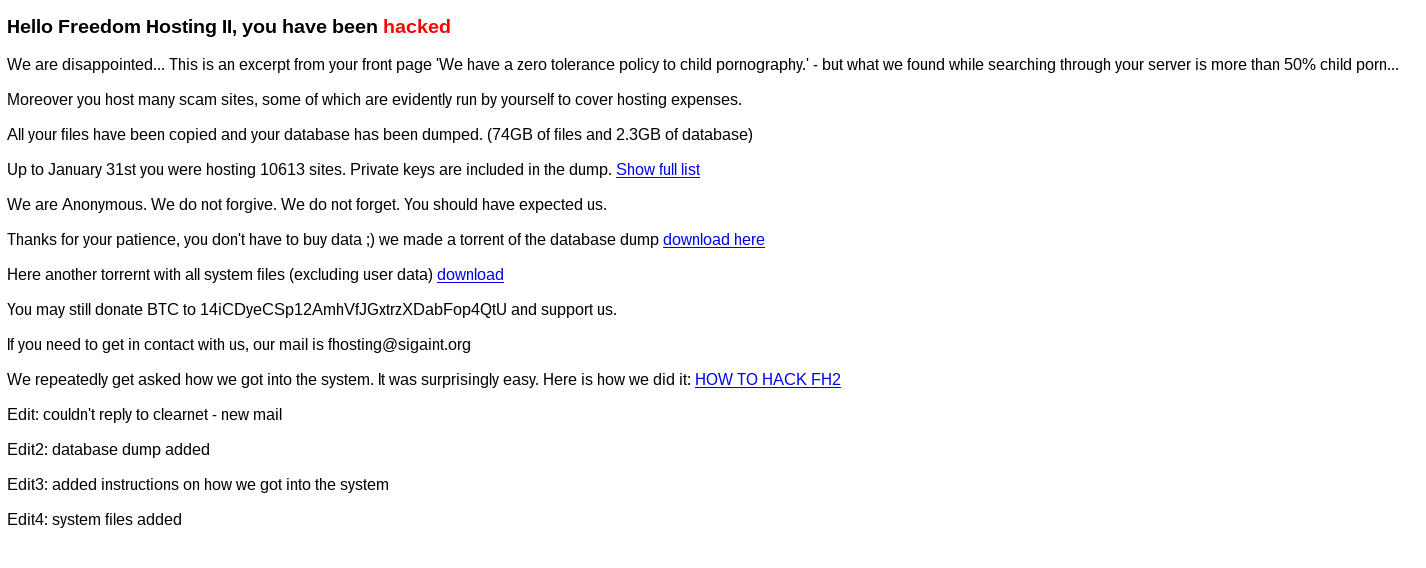
A screenshot of the message left by the hacker on Freedom Hosting II sites. Image: Screenshot by the author
On Saturday, the hacker claiming responsibility told me in more detail how and why they took down the service.
“This is in fact my first hack ever,” they said in an email sent from the same address posted to the hacked Freedom Hosting II sites. “I just had the right idea.”
The hacker said they first compromised the service on January 30, but only had read access; meaning they couldn’t change or delete files, but just see what sites were hosted.
“Initially I didn’t want to take down FH2, just look through it,” the hacker said. But they then allegedly found several large child pornography sites which were using more than Freedom Hosting II’s stated allowance. Usually, Freedom Hosting II has a quota of 256MB per site, but these illegal sites comprised of gigabytes of material, the hacker claimed.
“This suggests they paid for hosting and the admin knew of those sites. That’s when I decided to take it down instead,” the hacker said. At the time of writing, the hacker claims to have found 10 child pornography sites with approximately 30GB of files.
As for how they allegedly did it, the hacker has laid out a relatively simple 21 step process. In short, it starts by creating a new Freedom Hosting II site or logging into a current one, tweaking some settings in a configuration file, manually triggering a password reset for a target, turning on root access, and then logging back in with your new system privileges.
“20. reconnect via ssh as root; 21. enjoy,” the guide reads.
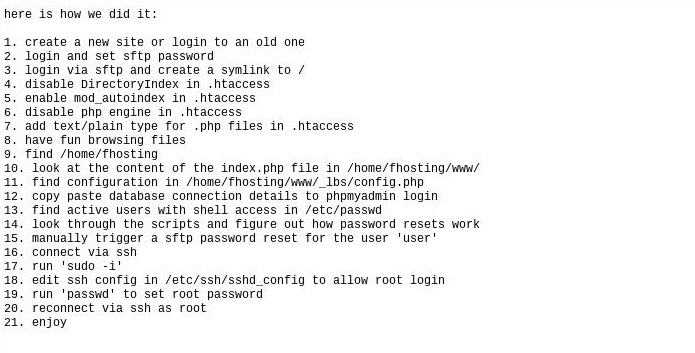
A screenshot of the method the hacker allegedly followed to take over Freedom Hosting II. Image: Screenshot by the author
The hacker said they had released a dump of system files from Freedom Hosting II, but not user data. They didn’t want to publicly distribute this because, as mentioned, it allegedly contains a high amount of child pornography. But the hacker said he will provide a copy to a security researcher who will then hand it to law enforcement.
The feds, however, might not be all that pleased. In recent years, when law enforcement agencies such as the FBI have taken over dark web sites or hosting providers, they have then tried to identify individual users by deploying malware. The FBI did this with the original Freedom Hosting—the agency used a hacking tool to grab visitors’ IP addresses. They used this tactic because even when in control of a Tor hidden service, law enforcement typically can’t see where each user is connecting from.
But now with the plethora of Freedom Hosting II child pornography sites shut down, the feds might not be able to use that sort of tactic at all. There still may be clues as to who operated each site within the Freedom Hosting II data, however.
This certainly isn’t the first time digital vigilantes have targeted child pornography sites on the dark web either. Another Anonymous-linked campaign hunted out abusers, and in 2014, a hacker deleted links to child pornography on a popular Tor-based wiki.
“If there is ever going to be a chance like that again, I won’t say no to taking them down, but I do not plan to do so,” the hacker said.
More
From VICE
-

Dave Fleetham/Design Pics Editorial/Universal Images Group via Getty Images -

Photo by Sean Gallup/Getty Images -

Westend61/Getty Images -

Simone Joyner/Getty Images
