Image: Shutterstock
Hacking back, when companies retaliate against cybercriminals, likely happens a lot more than the public realises. Whether a firm decides to gather intelligence on who is attacking its customers, or perhaps wipe stolen data from a server, hacking back is controversial.And people typically don't tweet about it. On Wednesday, encrypted email provider ProtonMail claimed it had hacked someone who was impersonating its service in phishing emails, and the company then swiftly deleted the tweet.Early Wednesday morning, the security researcher known as x0rz tweeted out a series of screenshots allegedly showing someone sending emails that directed targets to a fake ProtonMail login screen."You have an overdue invoice," the message read.In response, ProtonMail said it had taken action."We also hacked the phishing site so the link is down now," ProtonMail tweeted.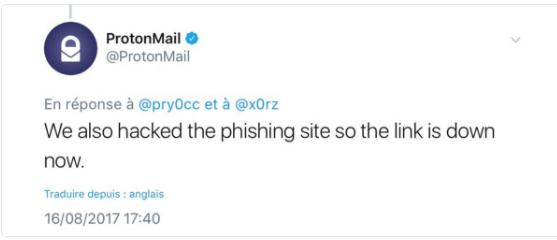 Depending on the context and what exactly the retaliating organization did, hacking back can be illegal. Hacking could violate the Computer Fraud and Abuse Act, or perhaps even wiretapping legislation. A recently proposed bill would attempt to legalize the practice.ProtonMail swiftly deleted its tweet, but not before x0rz could grab and subsequently tweet a screenshot. x0rz then deleted his own tweet at the request of ProtonMail.A ProtonMail spokesperson told Motherboard in an email that the company's hack back tweet, "was fueling unsubstantiated rumors and speculation about what may or may not have happened.""For reasons that you can probably understand, we do not really comment on the record regarding phishing attempts, and we cannot confirm nor deny if anything happened."Regardless, the phishing link is no longer active."We are glad to see that this phishing link (plus phishing links for Google and Yahoo) are no longer active," the rep added, "and that the owner of the site has gotten the assistance they need to secure their server."Got a tip? You can contact this reporter securely on Signal at +44 20 8133 5190, OTR chat at jfcox@jabber.ccc.de, or email joseph.cox@vice.com.Get six of our favorite Motherboard stories every day by signing up for our newsletter.
Depending on the context and what exactly the retaliating organization did, hacking back can be illegal. Hacking could violate the Computer Fraud and Abuse Act, or perhaps even wiretapping legislation. A recently proposed bill would attempt to legalize the practice.ProtonMail swiftly deleted its tweet, but not before x0rz could grab and subsequently tweet a screenshot. x0rz then deleted his own tweet at the request of ProtonMail.A ProtonMail spokesperson told Motherboard in an email that the company's hack back tweet, "was fueling unsubstantiated rumors and speculation about what may or may not have happened.""For reasons that you can probably understand, we do not really comment on the record regarding phishing attempts, and we cannot confirm nor deny if anything happened."Regardless, the phishing link is no longer active."We are glad to see that this phishing link (plus phishing links for Google and Yahoo) are no longer active," the rep added, "and that the owner of the site has gotten the assistance they need to secure their server."Got a tip? You can contact this reporter securely on Signal at +44 20 8133 5190, OTR chat at jfcox@jabber.ccc.de, or email joseph.cox@vice.com.Get six of our favorite Motherboard stories every day by signing up for our newsletter.
Advertisement

