Image:
When an Israeli entrepreneur went into a meeting with the infamous spyware vendor NSO, company representatives asked him if it would be OK for them to demo their powerful and expensive spying software, known as Pegasus, on his own phone.The entrepreneur, who spoke to Motherboard on condition of anonymity because he was not authorized to talk about the meeting, agreed, but said that NSO would have to target his other iPhone, which he brought with him and had a foreign phone number. He gave NSO that phone number and put the phone on the desk.After “five or seven minutes,” the contents of his phone’s screen appeared on a large display that was set up in the meeting room, all without him even clicking on a malicious link, he said.“I see clicking on all kinds of icons: email icon, SMS icon, and other icons,” he told Motherboard. “And suddenly I saw all my messages in there and I saw all the email in there and they were capable to open any information that was on my [iPhone].”The entrepreneur added that the NSO representatives accessed the microphone and the camera on his iPhone.That demonstration highlighted the power of an increasingly popular product among governments: software for remotely hacking phones in order to access communications and other data from targets. NSO is one of the main companies providing such a product to agencies around the world, including a number of customers that have used it to target human rights activists, nonprofit workers, and journalists in the United Arab Emirates and Mexico.The company operated in relative secrecy until researchers at Citizen Lab published a report on NSO in 2016 linking the company’s product to the hack of Ahmed Mansoor, a human rights activist in the United Arab Emirates.A source familiar with NSO told Motherboard that the company has around 600 employees, with approximately 250 working in research and development—which includes creating exploits in-house to break into phones. (Motherboard confirmed that the source has direct and current knowledge of the company.)The company has a group of engineers dedicated to making sure the company’s tools keep working because cell phone companies are in a constant “war” against government hacking providers “to block all those open windows that allow companies like NSO to go in,” according to the entrepreneur who attended the meeting, who was told that as part of the company’s sales pitch. NSO typically tries to keep a low profile. It has a minimal web presence and only attends select trade shows, though copies of its product brochures have leaked over the years.The source familiar with NSO added the company has around 100 employees in customer support.Human rights organizations have repeatedly and for years criticized NSO for selling its products to customers that targeted not just political dissidents like Mansoor, but journalists in Mexico, and an Amnesty International researcher. In the statement previously sent to Motherboard, NSO said its products are used to combat terrorism, child abduction, and other serious crimes.It’s up to them to approve the sale, and they have shut down deals that had already been closed and approved by the Israeli government, according to the source.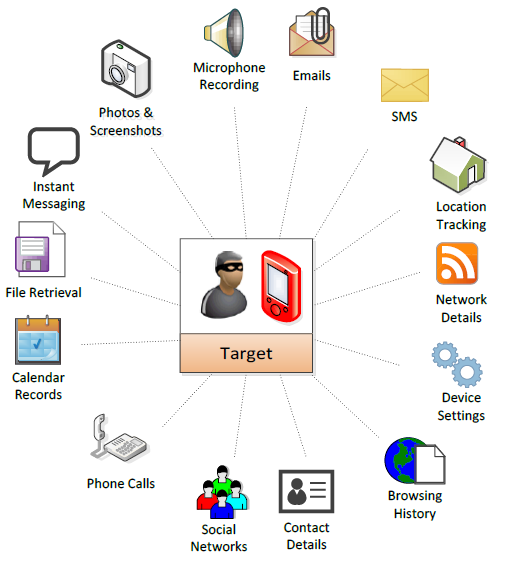 NSO employees visit their customers audit how the tools are being used, the source added. These visits involve interviews with operators and visits to the facilities. If the NSO employees see something they don’t like, they can escalate the issue, which can lead to the customer’s systems being shut down remotely, the source said.NSO’s competitor Hacking Team in the past also claimed to have a similar committee. But after the devastating breach the company suffered in 2015, leaked documents and emails revealed that the alleged external independent committee was simply a law firm hired by Hacking Team to make sure its deals did not go against local export laws. Hacking Team continued to sell to a slew of highly controversial customers, including Sudan.That’s why NSO will have to do better to convince its critics.“NSO Group’s claims about ‘strict due diligence’ and a supposed ‘Business Ethics Committee’ are implausible in the face of the facts,” Citizen Lab’s director Ron Deibert told Motherboard. “Our research on the UAE, Mexico, and, more recently, targets of espionage at Amnesty International—in sum, dozens of targets that are neither criminals nor terrorists— demonstrate their ineffectiveness.”Amit Serper, an Israeli security researcher at Cybereason who was invited for a job inteview at NSO, is skeptical about the company’s ability to avoid customers that will abuse its tools. (Serper said he has no direct knowledge of abuses.)“It’s like Hacking Team,” Serper told Motherboard in an online chat. “Those companies always end up doing business with the wrong people—because money.”Regardless, NSO’s business is booming, and that’s because its products are capable of impressing those who see them in action.“I didn't see it coming and everything was on the wall in five minutes,” the entrepreneur said.Correction: This story has been updated to clarify that Serper was invited to a job interview at NSO, not offered a job. We regret the error.Solve Motherboard’s weekly internet-themed crossword puzzle: Solve the Internet.
NSO employees visit their customers audit how the tools are being used, the source added. These visits involve interviews with operators and visits to the facilities. If the NSO employees see something they don’t like, they can escalate the issue, which can lead to the customer’s systems being shut down remotely, the source said.NSO’s competitor Hacking Team in the past also claimed to have a similar committee. But after the devastating breach the company suffered in 2015, leaked documents and emails revealed that the alleged external independent committee was simply a law firm hired by Hacking Team to make sure its deals did not go against local export laws. Hacking Team continued to sell to a slew of highly controversial customers, including Sudan.That’s why NSO will have to do better to convince its critics.“NSO Group’s claims about ‘strict due diligence’ and a supposed ‘Business Ethics Committee’ are implausible in the face of the facts,” Citizen Lab’s director Ron Deibert told Motherboard. “Our research on the UAE, Mexico, and, more recently, targets of espionage at Amnesty International—in sum, dozens of targets that are neither criminals nor terrorists— demonstrate their ineffectiveness.”Amit Serper, an Israeli security researcher at Cybereason who was invited for a job inteview at NSO, is skeptical about the company’s ability to avoid customers that will abuse its tools. (Serper said he has no direct knowledge of abuses.)“It’s like Hacking Team,” Serper told Motherboard in an online chat. “Those companies always end up doing business with the wrong people—because money.”Regardless, NSO’s business is booming, and that’s because its products are capable of impressing those who see them in action.“I didn't see it coming and everything was on the wall in five minutes,” the entrepreneur said.Correction: This story has been updated to clarify that Serper was invited to a job interview at NSO, not offered a job. We regret the error.Solve Motherboard’s weekly internet-themed crossword puzzle: Solve the Internet.
Advertisement
Pegasus can infect fully up-to-date Android and iPhone devices, and siphon a target’s emails, Facebook chats, and photos; pick up their GPS location and phone calls, and much more. NSO provides this toolkit, and then customers—law enforcement or intelligence agencies—deploy it themselves on their targets. As the New York Times recently reported, NSO demos its products to potential clients. The company is currently facing a number of lawsuits, including allegations it participated in illegal hacking operations itself.Got a tip? You can contact Lorenzo Franceschi-Bicchierai securely on Signal on +1 917 257 1382, or OTR on lorenzofb@jabber.ccc.de; and Joseph Cox on Signal on +44 20 8133 5190, or OTR on jfcox@jabber.ccc.de. Details on our SecureDrop, a system to anonymously submit documents or information, can be found here.
Advertisement
Advertisement
On Tuesday, researchers from Citizen Lab published a report saying it had found NSO’s Pegasus product being used in 45 countries, including in the United States.In a statement sent to Motherboard, NSO pushed back and said many of the countries listed by Citizen Lab were not customers, and said that its product cannot work in the United States. Earlier research has noted that Pegasus has a so-called “suicide” feature, which can disable the customer’s deployment of the malware. The source familiar with NSO elaborated, and said this can trigger if the customer is authorized to use the product against targets in one country but the target moves into another.Worldwide, NSO’s customers have purchased the capability to target between roughly 350 to 500 devices (15 to 30 per customer), according to the source. More potential customers approached NSO after the first Citizen Lab report on NSO’s tools being used to target Mansoor, the source said.For every potential sale, NSO has to get explicit permission—an export license—from Israel’s Ministry of Defense. With that green light, the company then asks a so-called business ethics committee to approve the sale.“NSO’s Business Ethics Committee, which includes outside experts from various disciplines, including law and foreign relations, reviews and approves each transaction and is authorized to reject agreements or cancel existing agreements where there is a case of improper use,” NSO said in the statement. The source familiar with NSO said the committee includes two lawyers who are experts in human rights, and three former US officials.Read more: Hacking Team Is Still Alive Thanks to a Mysterious Investor From Saudi Arabia
Advertisement

Advertisement

