In August 2016, Apple's head of security Ivan Krstic stole the show at one of the biggest security conferences in the world with an unexpected announcement."I wanna share some news with you," Krstic said at the Black Hat conference, before announcing that Apple was finally launching a bug bounty program to reward friendly hackers who report bugs to the company.The crowd erupted in enthusiastic applause. But almost a year later, the long-awaited program appears to be struggling to take off, with no public evidence that hackers have claimed any bug bounties.
Advertisement
The iPhone's security is so tight that it's hard to find any flaws at all, which leads to sky-high prices for bugs on the grey market. Researchers I spoke to are reluctant to report bugs both because they are so valuable and because reporting some bugs may actually prevent them from doing more research."People can get more cash if they sell their bugs to others," said Nikias Bassen, a security researcher for the company Zimperium, and who joined Apple's program last year. "If you're just doing it for the money, you're not going to give [bugs] to Apple directly."Patrick Wardle, a former NSA hacker and researcher at Synack who now specializes in MacOS research and was invited to the Apple bug bounty program, agreed. He said that iOS bugs are "too valuable to report to Apple."
In addition to Wardle and Bassen, I spoke to eight bug hunters in the program after granting them the condition of anonymity, which they requested to talk freely about the confidential details of the program. All of them said they have yet to report a bug to Apple, and none of them know of anyone who has. Apple declined to comment for this story.In September 2016, Apple flew Wardle, prominent iPhone jailbreaker Luca Todesco, and a small, select, group of white-hat hackers to its Cupertino headquarters.During their stay, Apple pitched the researchers on collaborating with the company by joining the bug bounty program. Apple security employees gave presentations, took the researchers out for dinner, and gave them a chance to chat and discuss their work. Even Craig Federighi, Apple's senior vice president of software engineering, made a surprise appearance to meet and greet the researchers, according to two sources who attended."If you're just doing it for the money, you're not going to give [bugs] to Apple directly."
Advertisement
This was a big shift, as security researchers and experts had long complained that Apple was the last major holdout among tech giants without a bug bounty program. Microsoft, Google, Facebook, and countless other smaller companies have had programs for years, dishing out sometimes lucrative rewards to independent hackers who choose to report vulnerabilities instead of using them for nefarious purposes."Apple doesn't like to ship things—including bug bounty programs—until they get them right. They're perfectionists," a former Apple employee who worked on security and asked to remain anonymous because of his non-disclosure agreement, told me.Last year, Apple pushed back against the FBI for months as it resisted an order to help the feds break into the iPhone of the San Bernardino shooter, who killed 14 people and injured 22 in December of 2015. The FBI eventually got into the phone, but not with Apple's help. Instead, the FBI paid for a costly exploit found by unknown, independent researchers. As The New York Times argued at the time, perhaps one reason hackers had exploits to sell to the FBI was that they had little incentive to report them to Apple instead.Though the announcement of the program was public, nearly everything else about it has been rolled out with Apple's typical secrecy. For now, the program is invite-only.The researchers who received an invite to join have had a chance to earn rewards ranging from $25,000 to $200,000 for bugs in iOS and MacOS, according to Krstic's talk.
Advertisement
A slide from Ivan Krstic's talk at Black Hat in 2016. (Image: Apple)
That might sound like a lot of money. But one of the reasons why the researchers we talked to aren't itching to report bugs is that Apple's rewards aren't as high as they could or maybe should be. In the private, gray market, where companies such as Zerodium buy exploits from researchers and sell them to their customers, a method comprised of multiple bugs that can jailbreak the iPhone is valued at $1.5 million. Another firm, Exodus Intelligence, offers up to $500,000 for similar iOS exploits. These companies claim to sell only to corporations to help them protect their networks, or to law enforcement and intelligence agencies to help them hack into high-value targets.It's possible that some hackers have taken advantage of Apple's bug bounty program and simply chose not to discuss it publicly, but the agreement that Apple asked researchers to sign if they wanted to participate in the program didn't strictly forbid them from discussing exploits they discovered. The agreement, which one of the researchers shared with me, only asks the researchers to wait until the bug is fixed and that the researchers "share" what they want to say with Apple before discussing the vulnerability publicly. Normally, researchers are happy to receive public recognition for their finds, both for the bragging rights, and because it helps build their resume as a hacker skilled enough to find flaws in some of the world's most secure software.
Advertisement
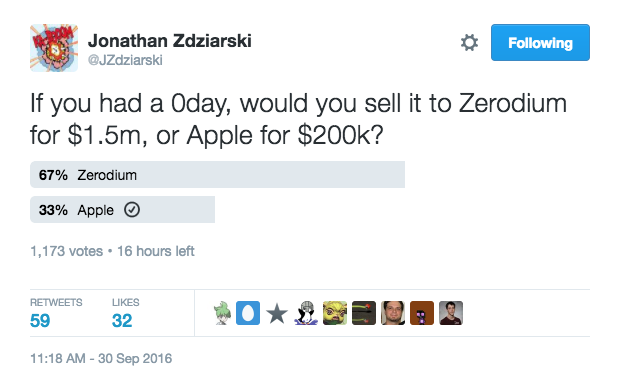
"Apple has to compete with the true value for the bugs they want to buy," Dan Guido, the CEO of the cybersecurity research firm Trail Of Bits, told me. "They're trying to buy game-over stuff at $200,000, but it's just worth more than that."In other words, the economics of the bug bounty are just not worth the trouble.Guido, who has done research on iOS security in the past, explained that Apple systems are so secure that finding a bug worth $200,000 is an unlikely prospect even if one can spend weeks or months on the search. That's why many don't bother looking, to avoid wasting a lot of time for no reward.
But it's not just about the immediate reward. iOS is such a complex, locked-down, and secure operating system that simply to inspect and do research on it, one needs multiple, unpatched, zero-day bugs, perhaps even a full-fledged jailbreak, according to researchers. In other words, you need unknown bugs just to find bugs in other parts of the operating system that might be otherwise locked.That's why some prefer to keep their bugs and continue doing research rather than handicapping themselves for a reward of few thousand dollars."Nobody is going to kill bugs unless they're fucking dumb," Luca Todesco, a well-known iPhone jailbreaker, told me a few months ago. "Just because they will kill their own future […] If I kill my own bugs then I'm not able to do my own research.""Nobody is going to kill bugs unless they're fucking dumb."
Advertisement
(Image: Lorenzo Franceschi-Bicchierai/Motherboard)
"Either you report and kill your own bugs, or you decide not to report the bugs so that you don't complicate your own life and you can keep doing research," another researcher who was invited to Apple's bug bounty program said. "Or you go to an independent company that pays for bugs so you don't waste two or three bugs for a bounty of just $50,000."While the researchers were visiting Cupertino, they asked Apple's security team for special iPhones that don't have certain restrictions so it's easier to hack them, according to multiple people who attended the meeting. These devices would have some security features, such as sandboxing, disabled in order to allow the researchers to continue doing their work. One researcher described them as "developer devices."But Apple, for now, isn't willing to provide those special devices, according to three researchers who recounted the exchange.Until Apple provides those devices, or invites more people to participate, the bug bounty program will have a hard time attracting serious attention from independent white-hat iPhone hackers."Apple tried something new again, offered huge payouts for fully functioning attacks, but they didn't read the bounty market properly or understand people's incentive for helping them," Guido said.In a way, the lack of bug submissions should also be seen as a testament to the security of the iPhone, but also as a sign the program needs changes, and perhaps more people looking for bugs, according to Guido."[Apple] broadcast this message that 'hey this program is only for certain people,' but in reality they want to engage with everybody," Guido said. "They need to do something they're bad at: they need to get the word out."Get six of our favorite Motherboard stories every day by signing up for our newsletter.
