Mathew Solnik stood next to two of the best iPhone hackers in the world and addressed the question the hundreds of people watching him were all wondering.“The white elephant in the room: How exactly did we get it?” Solnik, a well-known security researcher, said as he wrapped up one of the most anticipated talks at the Black Hat security conference in Las Vegas in early August 2016. In attendance, among hundreds of security professionals and hackers, were researchers from a company that sells iPhone-cracking services to cops around the world, and Apple’s own employees.
Advertisement
The thing that his team had been able to analyze for the first time was the iPhone’s Secure Enclave Processor (SEP), which handles data encryption for the iPhone. How they were able to do this was a valid question given Apple’s notorious secrecy, and the fact that the SEP is one of the most important and most closely guarded components of the iPhone, the most secure smartphone on the market.“Well, you get to ask us next time we talk,” Solnik added. (Solnik said the same when I approached him after the talk.)There was no next time: The team has never publicly discussed its methods.Now, more than two years later, Motherboard has learned how the team did it. During our investigation, we also discovered how other iPhone hackers research the most secure components and processes of the device.
Solnik’s team used a “dev-fused” iPhone, which was created for internal use at Apple, to extract and study the sensitive SEP software, according to four sources with specific knowledge of how the research was done. Dev-fused devices are sometimes called prototypes in the security research industry. They are essentially phones that have not finished the production process, or have been reverted to a development state.In other words, they are pre-jailbroken devices.These rare iPhones have many security features disabled, allowing researchers to probe them much more easily than the iPhones you can buy at a store. Since the Black Hat talk, dev-fused iPhones have become a tool that security researchers around the world use to find previously unknown iPhone vulnerabilities (known as zero days), Motherboard has learned.“It's kind of the golden egg to a jailbreaker.”
Advertisement
Listen to CYBER on Apple Podcasts, Google Podcasts, Stitcher, Spotify, Overcast, Pocket Casts, or on the RSS feed.Dev-fused iPhones that were never intended to escape Apple’s production pipeline have made their way to the gray market, where smugglers and middlemen sell them for thousands of dollars to hackers and security researchers. Using the information gleaned from probing a dev-fused device, researchers can sometimes parlay what they’ve learned into developing a hack for the normal iPhones hundreds of millions of people own.During Motherboard’s months-long investigation, I spoke to two dozen sources—security researchers, current and former Apple employees, rare phone collectors, and members of the iPhone jailbreaking scene—about the underground trade of dev-fused iPhones and their use in the iPhone hacking community. I used one of these devices and obtained “root” access on it, giving me almost total control over the phone; gaining root access allows researchers to probe many of the phone’s most important processes and components. And I learned that these devices are used by some of the highest-profile companies and independent experts that research and hack iOS to find valuable bugs that may later be exploited by governments and law enforcement agencies.
A dev-fused iPhone, connected to a Mac with a special cable, boots up. (Image: Motherboard)At BlackHat, Solnik and his two former colleagues David Wang and Tarjei Mandt—also known as Planetbeing and Kernelpool in the iPhone jailbreaking community—blew the doors off the SEP with the impressive and technical talk, which delved into, for example, how the phone’s application processor and SEP communicate using a “secure mailbox,” the SEP’s “bootflow,” and the specific “opcodes” that Apple uses to read information from the processor.
Advertisement
For iPhone hackers, the presentation was a godsend. At the time, Patrick Gray, who hosts an influential infosec podcast, described it as a “how2pwn guide” for the SEP, and thus, the iPhone.One reason the iPhone is so hard to hack is that Apple makes it almost impossible to study how the SEP and other key components work. That’s because the SEP operating system is encrypted, and—in theory—cannot be extracted or reverse engineered from a regular iPhone. But from a dev-fused device it’s possible, and has been repeated since Solnik’s talk by other researchers.“Wish I could say that they succeeded in pwning the system, but like many in the field [Solnik’s team] leveraged specific prototypes,” an iPhone jailbreaker who asked to be identified as Panaetius told Motherboard. Panaetius did not want to be identified given that he has also used dev-fused devices and is worried Apple may go after him.A person who formerly worked in Apple’s security team told Motherboard that he approached Wang after the talk at the conference. When he asked Wang how they managed to study the SEP, Wang told him that “Solnik got a dev-phone and dumped the firmware through standard Apple tools.”An independent iOS security researcher, who spoke on condition of anonymity in order not to damage his reputation within the jailbreaking community, said “Solnik was full of dev-fused [iPhones],” at the time of the SEP talk.
Advertisement
Another iOS security researcher, who also asked not to be identified, said he saw Solnik’s dev-fused devices and the proprietary cables used to work on them in the lead up to the SEP talk at Black Hat.Solnik, Wang, and Mandt, did not respond to multiple requests for comment. (At the time of the talk, Wang and Mandt were working for Azimuth, an Australian company that provides top-end hacking tools to governments such as the USA, Canada and the UK. Solnik had just left Azimuth.) Solnik was the subject of an episode of Phreaked Out, Motherboard’s 2014 documentary series about hacking.At the time, they may have been the first ones to get to the SEP, but thanks to the proliferation of dev-fused iPhones, others have repeated their feat. Lisa Braun, a pseudonymous independent iOS researcher, recently claimed to have dumped the SEP from an iPad Air 2 prototype.And he is not the only one.Got a tip? You can contact this reporter securely on Signal at +1 917 257 1382, OTR chat at lorenzofb@jabber.ccc.de, or email lorenzo@motherboard.tv
A few dev-fused iPhones, collected by Giulio Zompetti. (Image: Giulio Zompetti)
According to five sources in the iPhone hacking world, Cellebrite, a forensic firm that sells devices that can unlock iPhones, has purchased and used dev-fused devices to develop its products. Cellebrite did not respond to a request for comment.Chris Wade, the cofounder of Corellium, a startup that sells a product that allows users to create virtual instances of almost any iOS device in the world, has also gotten his hands on these devices, according to three sources in the iPhone hacking world and three sellers.
Advertisement
Wade, who is known as cmw in the jailbreaking community, told Motherboard he has never purchased a dev-fused device. He admitted having “played” with them at a conference, but denied using them in the development of Corellium. (In a 2016 tweet, however, Wade joked about owning “iPhone prototypes.”)“I want to be 100 percent clear we didn’t/don’t use dev phones @ Corellium. We don’t buy stolen Apple stuff!” Wade told Motherboard in an online chat. “I spent years working on Corellium and we never needed them. Using stolen dev phones is 100 percent the best way to get Apple to sue you or just fuck your life up.”Before Solnik’s Black Hat talk, Apple had yet to provide decrypted kernels to the public. Analyzing the kernel is a key step to hacking the iPhone and to understanding how iOS really works under the hood. And these dev-fused iPhones, available on the gray market for four or five figures, are the perfect tool to do that.“If you are an attacker, either you go blind or with a few thousand dollars you have all you need,” Luca Todesco, one of the most well-known iOS security researchers in the world, told Motherboard, referring to people who buy dev-fused iPhones. “Some people made the second choice.”Other researchers in the community told Motherboard that dev-fused devices are widely used in the iPhone hacking scene by researchers looking for zero day vulnerabilities.As Mandt put it in a Tweet in July of 2017, “anyone with a bit of effort and money can get hold of a switchboard device.” (“Switchboard devices” are another term for some dev-fused phones, which refers to the proprietary operating system they run.)
Advertisement
While the devices are indeed rare, if you go looking for them, they’re not hard to find.THE VENDORS“I’m here,” he texted me as I nervously looked around in the crowd of people criss-crossing a busy street in downtown Manhattan.I looked up and saw a slender man with long dark hair, a colorful hat; and—of course—he was holding an iPhone. I followed him to his workshop nearby. To open the door, he used a fingerprint reader that he said he made and programmed himself. Inside the workshop, there’s a handful electric skateboards, two fish tanks, and a sign that reads “If you taka my space I breaka your face.”The man is one of the few people in the world who openly advertises and sells dev-fused iPhones. He has a Twitter account called “Apple Internal Store,” but doesn’t share his real name because he is concerned Apple may go after him. He openly advertises dev-fused and other prototype iPhones for sale: One type of dev-fused iPhone X costs $1,800, for example. After reaching out on Twitter, he agreed to meet with me.The seller said he’s sold to several security researchers, and believes that many big security firms that hack iPhones have them.“Those people they don’t care about money. They don't care about the price.” he said. “Whatever it is, the company buys it.”He’s defensive when I ask how he got the phones.“Well, I didn’t steal any device. I actually paid for them,” he said as he showed off a bunch of dev-fused devices. “As long as you don’t break [Apple’s] balls, or show an iPhone 11 prototype, or an unreleased device, they’re most likely cool with that.”
Advertisement
On the back of dev-fused iPhones seen by Motherboard, there’s a QR-code sticker, a separate barcode, and a decal that says “FOXCONN,” referring to the factory that makes iPhones and other Apple products. Otherwise, the phones look like normal iPhones. That standard iPhone experience ends when the phone is turned on. When booted up, you briefly see a command line terminal. And then when it loads, gone are the sleek icons and colorful backgrounds of iOS. The phone boots into an operating system known as “Switchboard,” which has a no-nonsense black background and is intended for testing different functionalities on the phone. The home screen is populated with icons for apps with names like MMI, Reliability, Sequencer, and Console, an app that allows you to open a command line terminal inside the iPhone.
A dev-fused iPhone mounted on a rig. (Image: Motherboard)
Clicking through these apps is at times frustrating as they’re made to be used via the command line terminal while connected to a computer. Most of them cannot be closed by tapping or swiping, meaning the phone needs to be turned off and back on to get back to the home screen. Switchboard’s apps suggest a playfulness that Apple doesn’t always let through on iOS. The icon for “Reliability” features a doge (from the meme) playing a musical keyboard. The app itself allows you to test the functionality of the phone’s cameras, speakers, microphone, battery, and ambient light sensors, among other functionalities. An app called “Ness” features the lead character from Nintendo’s game Earthbound. Though the iPhone wiki speculates it could be used to test the phone’s temperature; when I try to launch it, the phone turns off. An app called “Sightglass” used to have the logo for a San Francisco coffee roaster by the same name; it has been changed to a matrix of colored dots.
Advertisement
You can’t do too much with the phone on its own. But once you connect it to a Mac with a proprietary Apple USB cable called “Kanzi,” which can cost around $2,000 on the gray market, you are able to use other internal Apple software (that is widely shared in the jailbreaking community) to get root access on the phone and burrow deep into its software and firmware. The special cable is required because Apple uses a proprietary protocol for accessing certain data within the iPhone to debug the kernel and other hard-to-reach components.Two people showed Motherboard how to get root access on the phone we used; it was a trivial process that required using the login: “root” and a default password: “alpine.”Not all dev-fused devices look normal, though. Some of them come mounted on clunky-looking metal rigs that allow you to open them up like a pizza box to inspect the phone’s guts, look at the battery, motherboard, and other internal parts. One that I saw had external wires running from the rig to the inside of the device; the rig itself had what looked like RF connector ports attached to those wires, as well as external, metal volume and power buttons.Once I started looking for dev-fused iPhones, they weren’t that hard to find, provided you’re willing to shell out a few thousand bucks and aren’t worried about potentially pissing off Apple. Besides Apple Internal Store, there are other Twitter accounts that openly advertise them.
Advertisement
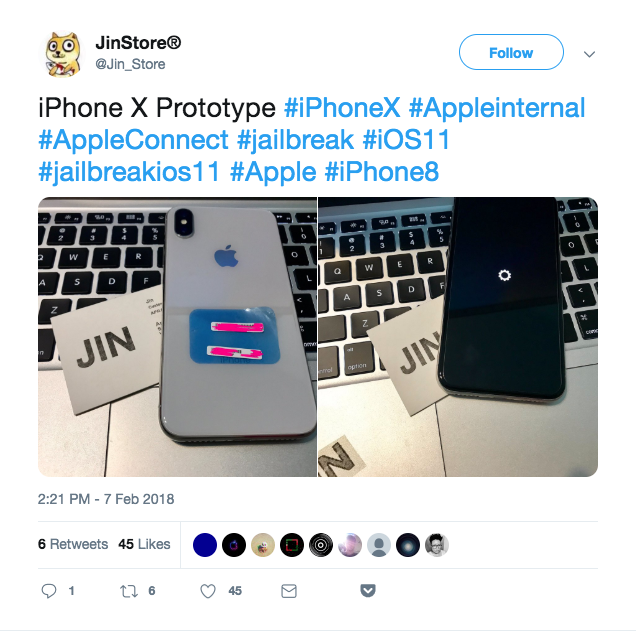
The owner of the Twitter account Jin Store, which claims to sell dev-fused or prototype iPhones, shared their catalog with Motherboard. A dev-fused iPhone 8 Plus costs $5,000, an iPhone XR $20,000, and an older iPhone 6 costs $1,300 (there are several different types of dev-fused devices that have different levels of security and varying features on them. The price of the dev-fused device depends on the security and features it includes.)In a conversation via WeChat, Jin said that they personally know Solnik, but declined to say whether he was a customer.The person behind another dev-fused store that advertises on Twitter, who goes by Mr. White, said he has “almost all” iPhone models. He also claimed to have sold “a lot of” dev-fused iPhones to security researchers.“I don't know how to get SEPROM,” Mr. White told me in an online chat, using another technical term for the SEP. “But I know that their research needs my equipment.”THE DEVICES THAT ESCAPE SHENZHENThough it’s possible to buy dev-fused iPhones from various sources, it’s not like there’s a huge supply of them. Outside of Apple and the security research industry, these devices are almost a complete unknown. Even finding any substantial online references to the term dev-fused is difficult.In a Hacker News thread prompted by a Motherboard investigation on the iPhone bug bounty program, former iPhone jailbreaker and current security researcher Will Strafach wrote that “Apple has dev-fused devices which use separate development certificates and keys.” An entry in the unofficial iPhone wiki also briefly mentions prototype devices. The page is introduced by a big red rectangle that warns readers that “acquiring a copy [of internal Apple software] without Apple's consent is illegal and may result in being scammed.”
Advertisement
The day after Solnik, Mandt and Wang’s talk, Apple’s head of security Ivan Krstić also spoke at Black Hat. A single line of his presentation slides referred to “development fused” iPhones, though he didn’t actually mention them during his talk. As far as we know, that’s the only time Apple has publicly acknowledged their existence. An Apple spokesperson declined to discuss these devices with Motherboard.When reached via Twitter, Krstić said that he could not talk about anything work related, and instead joked I could ask him about his “borderline-encyclopedic knowledge about preparing steak.”But despite being essentially a secret from the public, security researchers and hackers have known about and used these devices for years.“They are very popular among security researchers,” said a person who’s familiar with the supply chain of smuggled iPhones in China, who spoke on condition of anonymity to avoid putting his associates in China at risk. “I’ve had a number ask me and say they were willing to pay a significant amount of money to get dev phones.”
Andrew “Bunnie” Huang, a well-known hardware security researcher who wrote the ultimate guide to Shenzhen’s electronics markets, told Motherboard that he has seen some of these devices in China. Few people know exactly how they get from Foxconn, which manufactures iPhones, to Shenzhen’s markets. But they find a way there.“They are stolen from the factory and development campus.”
Advertisement
“They are stolen from the factory and development campus,” a person who sells these devices on Twitter told Motherboard.At times, Huang said, even the people who sell dev-fused devices in Shenzhen aren’t aware of how valuable they can be to hackers and security researchers.“The gray market guys don't even know what they sit on half the time,” Huang said in an online chat. “They are just trading trash for cash.”“It gives you a new attack surface that's not as heavily fortified,” Huang added. “They don't put the metaphorical lock on the door until the walls are built on the house, so to speak.”
A couple of dev-fused devices, collected by Giulio Zompetti. (Image: Giulio Zompetti)To be more technical, and unlike the iPhones you can buy at the Apple store, called “prod” or “production fused,” these devices allow their owners to boot into Switchboard. This software allows researchers to hack and reverse engineer different components of iOS. These would be usually off limits without hard-to-get vulnerabilities and a jailbreak, which is worth millions of dollars in today’s zero-day market.“Prod fused means there’s a specific pin on the board that is ‘blown’ in the production phase. The board checks that pin to see if the device is prod or not,” a former Apple employee who wanted to remain anonymous because he is bound by a non-disclosure agreement, told Motherboard. “If it isn’t, and the firmware is dev version, then certain features are enabled.”
Advertisement
With a proprietary Apple cable and the right skills, they’re the perfect iPhone hacker’s playground.In 2017, Motherboard reported that the best iPhone hackers in the world did not want to report bugs to Apple, even after the company promised six-figure rewards. One of the complaints the researchers had was that it was incredibly hard to find bugs without already knowing about other bugs. In other words, security researchers need iOS bugs—those that allow them to jailbreak the device and disable security features—just to be able to do their research. If independent researchers were to report bugs to Apple, in their view, they could lead Apple to fix the flaws they rely on to find other bugs.At the time, some of the researchers said that it’d be better if Apple gave them “developer devices.”As it turns out, some already had them.“It's kind of the golden egg to a jailbreaker,” according to Panaetius, who said he’s bought and re-sold several dev-fused devices. “Here’s a device where you can slap all the security mechanisms out of the way. Because there are still security mechanisms on a development fused device, but you can kind of just push them.”iPhone hackers, however, are not too keen to discuss the fact that they use them. Some told me that using them is like “cheating,” and others swore to me that they have never used them because it’d be perceived in the scene as being lame.“Many folks are very wary of these. Just because many do not want to deal with Apple’s allegedly vicious legal folks,” a security researcher who has been in the jailbreak community for years, and asked to be anonymous to discuss sensitive issues, told Motherboard.
Advertisement
Others aren’t nearly as concerned.THE COLLECTORSGiulio Zompetti, who calls himself a collector of iPhone prototypes, told me he has 14 dev-fused iPhones, as well as some iPods and iPads. He showed me many of them on a video chat.He said that while he plays around with his dev-fused devices, he doesn’t hack them—he only collects them.“For me it’s a bit of an investment. The older they are, the harder it is to find them,” Zompetti said in a phone call. “It’s just fun. The search of something that by itself is really hard to get.”“The goal is to reconstruct history,” Zompetti told me as he showed me some of his pieces, including an iPhone 5S that he said was dated just a couple of months after the release of the iPhone 5, the previous model.Another collector who showed me pictures of his devices told me they have too many devices to count.
Apple is well aware of the fact that dev-fused devices get traded around, according to five sources within and outside the company. Several sources both inside Apple and in the jailbreaking community believe that Apple has ramped up its efforts to keep these devices from escaping Foxconn and to go after people who sell them. It’s no surprise Apple knows that researchers covet these—some of them have even poked Apple publicly. Back in 2016, Solnik teased his great breakthrough on Twitter weeks before his Black Hat talk.“Who wants to see a security team jump?” he tweeted, along with a screenshot of a terminal window that showed Solnik had been able to obtain the Secure Enclave Processor firmware. “I’ll just leave this here.”The precise step-by-step of how Solnik, Wand, and Mandt, were able to decrypt and reverse engineer the firmware has never been discussed publicly. Their talk, however, was enough to attract Apple’s attention and boost the speakers’ careers and reputation within the iPhone security research community.
Mandt is still at Azimuth, whereas Wang moved to Corellium. Solnik, on the other hand, is himself a bit of a mystery. At the time of the SEP talk, he was heading his own startup, called OffCell, which was founded with the goal of becoming a government contractor providing offensive security tools and exploits to governments, according to several sources who know Solnik.In 2017, however, Solnik was hired by Apple to work on its security team, specifically on the so-called red team, which audits and hacks the company’s products. His talk at Black Hat had apparently impressed the folks at Cupertino. A few weeks later, however, he abruptly left the company, according to multiple sources.The full story of Solnik’s short stint at Apple is a closely-guarded secret. Motherboard spoke to dozens of people and was unable to confirm the specifics around his leaving the company; one source within Apple told me information about Solnik is “incredibly restricted,” and another confirmed that even within Apple, few know exactly what happened.Apple repeatedly declined to comment or respond to any questions regarding Solnik, but did not deny that Solnik worked there.In any case, the underground market for dev-fused iPhones is now flourishing. And, for now, Apple doesn’t seem able to stop the flood, despite the fact that these leaks are fueling a growing industry of iPhone hacking companies.“To be honest everyone benefits from Apple’s lousy supply chain management,” Viktor Oreshkin, an iOS security researcher, told Motherboard in an online chat. “Except Apple, obviously.”Listen to CYBER, Motherboard’s new weekly podcast about hacking and cybersecurity.