Image: Cathryn Virginia
The Weakest Link is Motherboard's third, annual theme week dedicated to the future of hacking and cybersecurity. Follow along here.Listen to Motherboard’s new hacking podcast, CYBER, here.
The rapid development of technology has had a direct effect on the lifespan of consumer electronics in recent years. Device makers have an economic incentive to shorten product life cycles, but technology enthusiasts who want to have the latest and greatest gadgets also contribute to the trend.Replacing phones and laptops every couple of years increases the privacy and security risk to consumers because many users don't properly wipe data from their devices before selling or disposing of them. That's not completely their fault as securely erasing data from modern devices is not as straightforward as one might think.Read on to find out why that is and how encryption can help mitigate those risks. Also, is selling your old devices a good idea or is it better to simply destroy them?Deciding how to get rid of a laptop, phone, or storage device in a way that doesn't risk stored data being compromised really depends on who's likely to be interested in that information and the length they might go to obtain it.The recommendations in this article are generally aimed at users who would want to protect their data from a regular cybercriminal or a curious buyer. Such individuals are unlikely to have the resources, skills, or even the interest to attempt sophisticated and time-consuming data recovery procedures. There’s simply not a big enough return on investment.Data sanitization is about risk mitigation: What is the value of the data you are trying to destroy and what are the resources of whoever might attempt to access that data?"For most consumers, it's probably enough just to make sure that they're not a low hanging fruit; that the effort it would cost to attempt to recover the data from the drive far exceeds the value of the drive itself and it's just easier to sell it for parts or put it back into service," said Greg Andrzejewski, the director of research and development at Gillware, a data recovery company whose services are used by Dell, Western Digital and other technology companies.On the other hand, if you're a political activist in a country with a repressive regime or a senior executive in a high-profile corporation, the resources and motivation of the people who might target you will be significantly different than what a regular consumer could face. In that case, it's best not to sell your old devices or to take them to recycling centers that might recondition them and put them back into circulation."The user has to think: What's the worst case scenario if someone did access a partial set of my data?" said Nathan Little, director of product development at Gillware Forensics, the digital forensics arm of Gillware. "Is that worth me selling my phone for $50 or is it safer for me just to keep it or physically destroy it and throw it in the dumpster?"Before we talk about data wiping, we should talk about encryption, because the best way to minimize data privacy risks when selling a laptop, a mobile phone, or some other computing device is to turn on disk or storage encryption as soon as you start using it.This will ensure that even if there’s some leftover data when you dispose of the device, it will be useless to someone who doesn't have the decryption key or the password that unlocks that decryption key. And, of course, encryption will also protect your data if the device gets lost or stolen.All major desktop operating systems support full-disk encryption. MacOS has FileVault, Linux has LUKS (Linux Unified Key Setup-on-disk-format) and Windows has BitLocker in the Pro and Enterprise versions and a more limited version called Device Encryption in Windows Home, if the device has a Trusted Platform Module (TPM) 2.0 dedicated crypto chip. There are also third-party open-source tools like VeraCrypt that can encrypt both external disks and the primary drive hosting the OS.Some of these solutions will encrypt the master decryption key with the user’s login password or with a separate password that needs to be entered when the system boots up, and will store it in a special region of the drive itself. Because of this, it’s important to use a long and hard-to-guess passphrase that cannot be easily cracked using brute-force methods.It also means that you should still wipe the storage device before selling or recycling it even if the data on it is encrypted. This will ensure the password-protected encryption key stored on the drive will be deleted and the data will be lost forever.Some storage devices are self-encrypting, their internal controllers using a specialized chip and firmware to encrypt data before writing it to the drive. However, these encryption implementations are not open-source or publicly documented, so it's hard to know whether they work correctly or not.In fact, a 2015 study of several external Western Digital hard disk drives (HDDs) with self-encrypting capabilities found serious implementation flaws that could have allowed attackers to recover data or decryption keys. The drives used USB bridge controllers that handled the cryptographic operations from different manufacturers, so the problem is not limited to a single vendor.The conclusion is that even if you have a self-encrypting drive (SED), it may still be a good idea to use another encryption solution on top of it to secure the data. The encryption features of modern operating systems are widely used and have been scrutinized by many security researchers over the years. VeraCrypt—a fork of the now-abandoned TrueCrypt software—has also been audited by security experts.Even if you just realize the importance of full-disk encryption now, it's not too late to turn it on. The sooner you do, the less likely it is that someone will be able to recover data from your device when you sell it or take it to a recycling center.But make sure to backup the recovery keys that your encryption software generates in a safe place and also back up your important files regularly, preferably to a secondary encrypted disk. If your drive fails before you dispose of it, no data recovery company will be able to help you if you don't have the recovery keys to your encrypted partitions.Hard disk drives store data on rotating disks called platters that are coated with magnetic material. They have been the standard storage medium in the computer industry for decades and are well understood, so various methods of "sanitizing," or securely erasing, data are available for them.There is even a command in the ATA specification—the standard communication interface between computers and disks—called SECURITY ERASE UNIT, or more commonly known as Secure Erase, that HDD and solid-state drive (SSD) manufacturers can implement. Executing the Secure Erase command on either a HDD or SDD will destroy data from all internal locations, returning it to a factory default state.WindowsFirst, it's worth noting that the default quick format operation built into Windows does not actually destroy data. It only clears the file system, which is an index of records that hold information about files and their physical locations on disk. A quick format will mark the mapped physical locations as free space that’s available for reuse, but the old data will remain in the physical sectors until it will slowly be overwritten by programs in the future. As such, a quick format doesn't count as data sanitization for devices intended to be discarded.Microsoft does provide the option to overwrite all of a disk’s sectors with zeroes, which will make it almost impossible, or at least commercially unsustainable, for data recovery firms to restore any usable data. This a functionality of the DiskPart command line utility, implemented as a “clean all” command.To use DiskPart against the primary disk that holds the operating system, you will need to boot from Windows installation media (CD or USB stick) and enter the recovery environment. Once there, you should select the Command Prompt option and then type “diskpart” to enter the DiskPart utility.
 The “list disk” command will list all available disks with a number (0, 1, etc.) that identifies each of them. Once you identify the disk you want to wipe from the list, type “select disk #”, where # is the number that corresponds to that disk. Then type “clean all” and be patient, as the operation can take a long time.Double check that you selected the correct disk, as the operation is irreversible. And also note that executing only the “clean” command, without the “all” parameter, will only destroy the first sector of the disk, which contains information about the disk partitions, but will not overwrite all sectors with zeroes.
The “list disk” command will list all available disks with a number (0, 1, etc.) that identifies each of them. Once you identify the disk you want to wipe from the list, type “select disk #”, where # is the number that corresponds to that disk. Then type “clean all” and be patient, as the operation can take a long time.Double check that you selected the correct disk, as the operation is irreversible. And also note that executing only the “clean” command, without the “all” parameter, will only destroy the first sector of the disk, which contains information about the disk partitions, but will not overwrite all sectors with zeroes.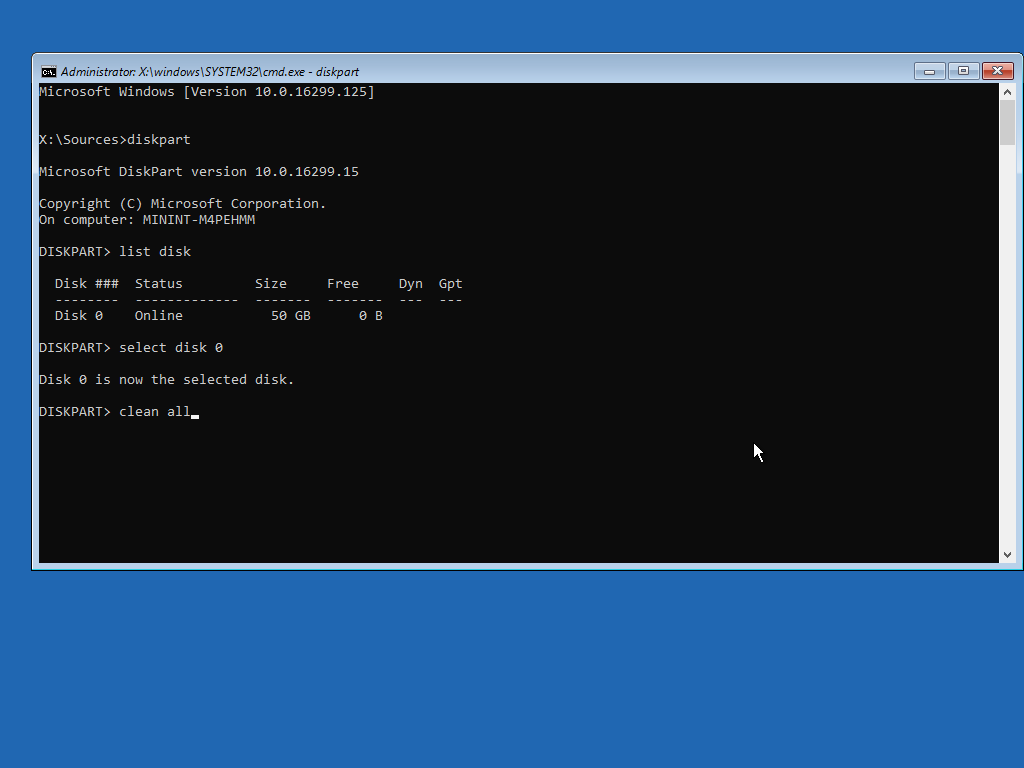 HDD makers provide their own specialized diagnostics programs such as Seagate SeaTools or Western Digital Data Lifeguard Diagnostics that include secure data erase, or zero-fill, functionality. This is also known as a zero-fill because it overwrites all of the disk’s sectors with zeroes, returning it to its factory default state.These vendor tools usually come in two versions: One that can be installed on Windows as a regular application and a DOS-based version that must be run from a bootable CD or USB stick. The latter is needed to erase a computer’s primary disk which contains the operating system, because you can't wipe an HDD from inside an OS that’s actively running from it.
HDD makers provide their own specialized diagnostics programs such as Seagate SeaTools or Western Digital Data Lifeguard Diagnostics that include secure data erase, or zero-fill, functionality. This is also known as a zero-fill because it overwrites all of the disk’s sectors with zeroes, returning it to its factory default state.These vendor tools usually come in two versions: One that can be installed on Windows as a regular application and a DOS-based version that must be run from a bootable CD or USB stick. The latter is needed to erase a computer’s primary disk which contains the operating system, because you can't wipe an HDD from inside an OS that’s actively running from it.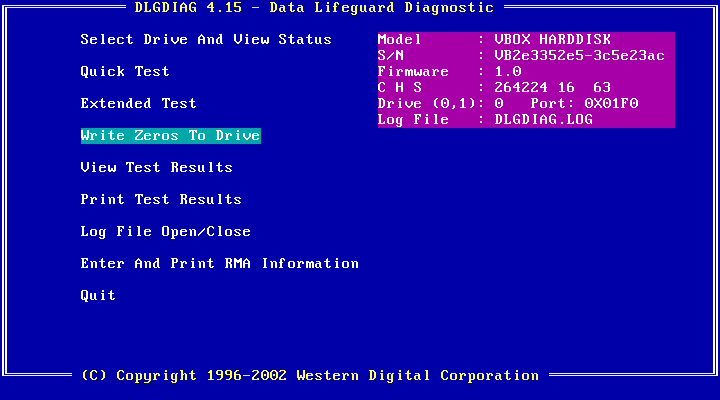 To create bootable CDs or USB sticks with such tools, users will have to follow the instructions provided for each tool. However, there’s an easier solution: There are community-maintained boot CDs that contain collections of system recovery, administration and diagnostic tools, including the utilities provided by HDD manufacturers and which can be hard to get nowadays because some drive makers have been bought by competitors over the years and their old websites and download links have disappeared.The actively updated Ultimate Boot CD (UBCD) is one example and it can be written to a USB thumb drive with tools such as Rufus or the Universal USB Installer. It also bundles other popular third-party data wiping tools like Darik's Boot and Nuke (DBAN), a program that implements more complex wiping routines like those specified in data sanitization guides from the US Department of Defense and other government agencies.
To create bootable CDs or USB sticks with such tools, users will have to follow the instructions provided for each tool. However, there’s an easier solution: There are community-maintained boot CDs that contain collections of system recovery, administration and diagnostic tools, including the utilities provided by HDD manufacturers and which can be hard to get nowadays because some drive makers have been bought by competitors over the years and their old websites and download links have disappeared.The actively updated Ultimate Boot CD (UBCD) is one example and it can be written to a USB thumb drive with tools such as Rufus or the Universal USB Installer. It also bundles other popular third-party data wiping tools like Darik's Boot and Nuke (DBAN), a program that implements more complex wiping routines like those specified in data sanitization guides from the US Department of Defense and other government agencies.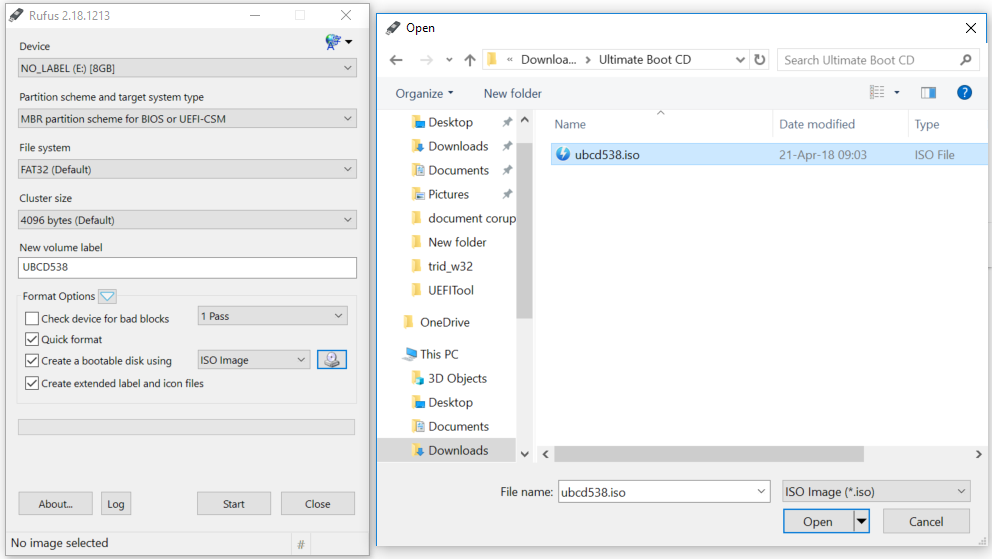 These standards require sensitive information, such as government confidential data, to be wiped by performing multiple rounds of full-disk overwrites using various data patterns, but they can take a very long time and are most likely overkill for regular users.
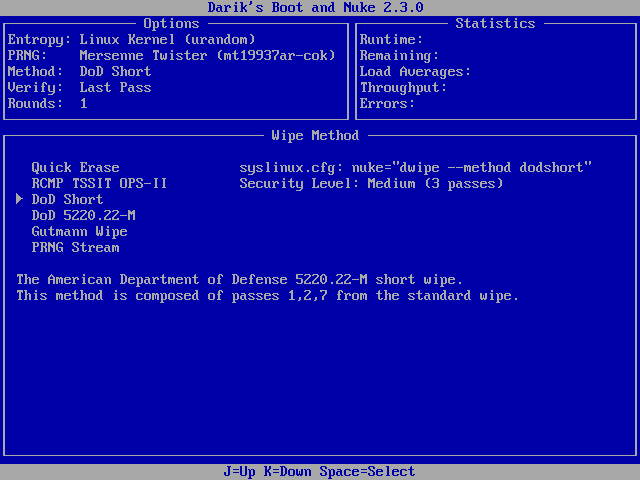
These standards require sensitive information, such as government confidential data, to be wiped by performing multiple rounds of full-disk overwrites using various data patterns, but they can take a very long time and are most likely overkill for regular users.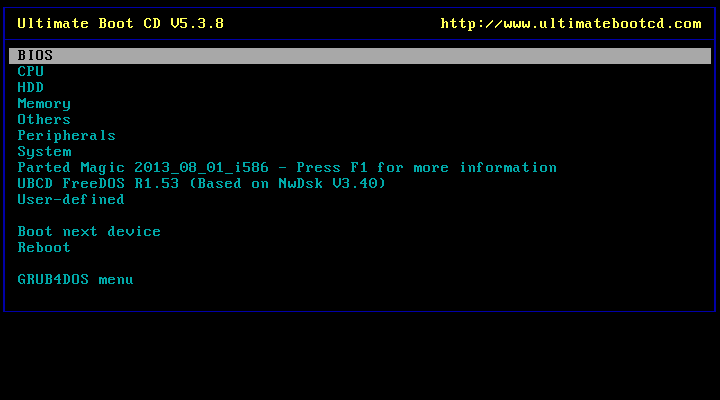

 MacOSThe Disk Utility in macOS (formerly OS X) provides multiple data erasure options for HDDs under “Security Options” including multipass overwrites that conforms to the DoD 5220.22-M specification.Inside MacOS the Disk Utility can be found under /Applications/Utilities/ and can be used to erase externally attached drives. To wipe a disk that contains the macOS boot volume, users can boot into Recovery mode and use Disk Utility from there. Note that the secure erase options will not be available for SSDs.
MacOSThe Disk Utility in macOS (formerly OS X) provides multiple data erasure options for HDDs under “Security Options” including multipass overwrites that conforms to the DoD 5220.22-M specification.Inside MacOS the Disk Utility can be found under /Applications/Utilities/ and can be used to erase externally attached drives. To wipe a disk that contains the macOS boot volume, users can boot into Recovery mode and use Disk Utility from there. Note that the secure erase options will not be available for SSDs.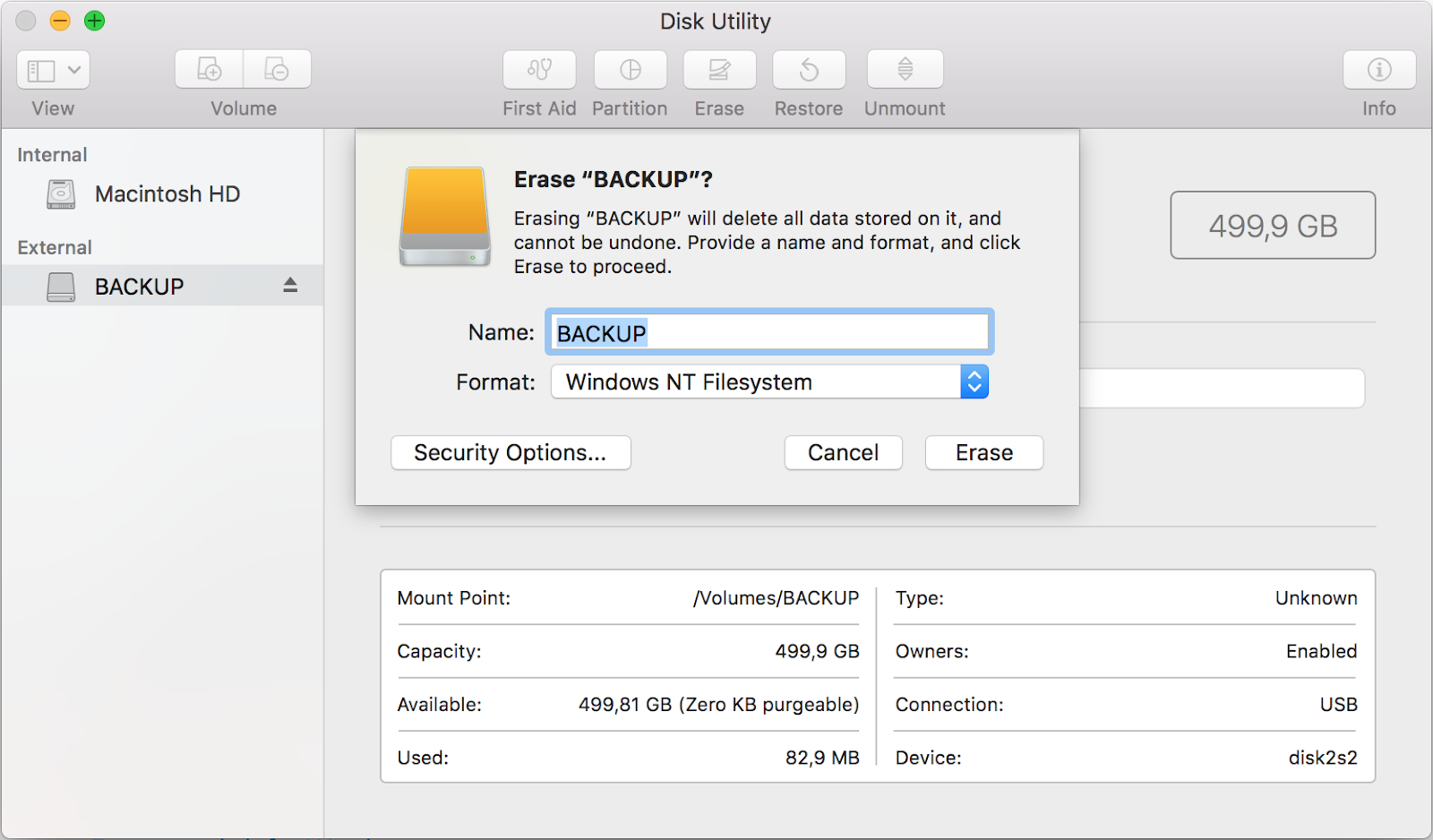
 When it comes to the solid-state drives that have replaced HDDs in many modern laptops, such as MacBooks and Windows ultrabooks, things get more complicated. These drives store data in flash memory chips rather than on magnetic platters and use complex storage management algorithms that make traditional data wiping methods like zero-fill or multipass overwrites much less reliable.SSDs have an internal flash translation layer that maps logical block addresses (LBAs) used by file systems, to pages, which are rows of physical cells in the memory chip. A block is made up of up to 256 memory pages.When applications want to overwrite existing data, SSDs do not perform an in-place update of the physical pages that contain the old data. Instead, they write the new data to empty pages because it's faster and to ensure an even wear of all memory cells. Then the SSD's flash translation layer updates the LBA internally so that programs see the new version of the data at the same location as before.This performance-enhancing trick causes old versions of the data to remain behind in what will now be considered stale pages. These will eventually be cleared when the other pages that make up the same block will also become stale or when their data will be intentionally moved to empty pages in other blocks.This process is known as garbage collection and is necessary so that entire blocks can be erased and put into use again. It's also the reason why SSDs are over-provisioned with spare blocks and why the TRIM command, which allows the OS to alert the SSD about invalid pages, was introduced.WindowsFor most consumers, the easiest solution to wipe an SSD is to identify its make and model and then use a utility provided by its manufacturer to execute an internal Secure Erase command (Intel, Samsung, Toshiba OCZ, SanDisk, Kingston, Crucial, Western Digital, Seagate, Corsair). Like with HDDs, this has to be performed from outside the operating system and will be executed by the firmware.Most of the SSD management applications provided by SSD makers need to be installed under Windows first and will have an option in their interfaces to create a bootable USB stick with a separate utility for secure erasure.
When it comes to the solid-state drives that have replaced HDDs in many modern laptops, such as MacBooks and Windows ultrabooks, things get more complicated. These drives store data in flash memory chips rather than on magnetic platters and use complex storage management algorithms that make traditional data wiping methods like zero-fill or multipass overwrites much less reliable.SSDs have an internal flash translation layer that maps logical block addresses (LBAs) used by file systems, to pages, which are rows of physical cells in the memory chip. A block is made up of up to 256 memory pages.When applications want to overwrite existing data, SSDs do not perform an in-place update of the physical pages that contain the old data. Instead, they write the new data to empty pages because it's faster and to ensure an even wear of all memory cells. Then the SSD's flash translation layer updates the LBA internally so that programs see the new version of the data at the same location as before.This performance-enhancing trick causes old versions of the data to remain behind in what will now be considered stale pages. These will eventually be cleared when the other pages that make up the same block will also become stale or when their data will be intentionally moved to empty pages in other blocks.This process is known as garbage collection and is necessary so that entire blocks can be erased and put into use again. It's also the reason why SSDs are over-provisioned with spare blocks and why the TRIM command, which allows the OS to alert the SSD about invalid pages, was introduced.WindowsFor most consumers, the easiest solution to wipe an SSD is to identify its make and model and then use a utility provided by its manufacturer to execute an internal Secure Erase command (Intel, Samsung, Toshiba OCZ, SanDisk, Kingston, Crucial, Western Digital, Seagate, Corsair). Like with HDDs, this has to be performed from outside the operating system and will be executed by the firmware.Most of the SSD management applications provided by SSD makers need to be installed under Windows first and will have an option in their interfaces to create a bootable USB stick with a separate utility for secure erasure.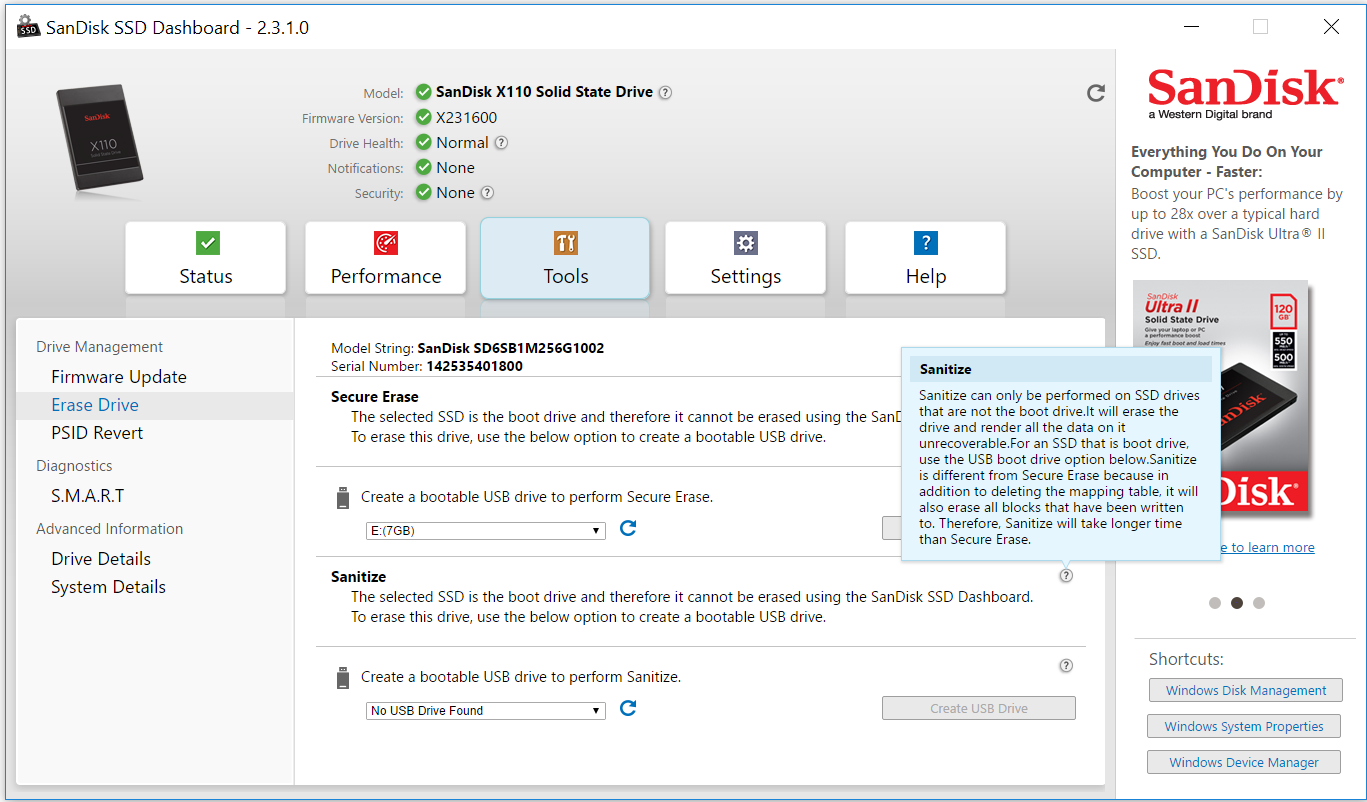 Third-party tools for executing the ATA Secure Erase command on both HDDs and SSDs include Parted Magic, a previously free bootable CD for partition management that now costs $11 to download, and HDDerase, a bootable DOS-based utility originally developed at the University of California San Diego’s Center for Memory and Recording Research, but which hasn’t been updated since 2008 and might not work with some drives or some configurations.The previously mentioned Ultimate Boot CD includes both HDDerase and the last free version of Parted Magic dating from 2013. Parted Magic is the better option because it has a graphical user interface for Secure Erase, but the last freely available version included in Ultimate Boot CD has some known issues that could brick drives and which have been resolved in later paid-only versions. The Linux hdparm utility can also be used to issue an ATA Secure Erase command, but is quite fiddly to use and comes with many warnings.
Third-party tools for executing the ATA Secure Erase command on both HDDs and SSDs include Parted Magic, a previously free bootable CD for partition management that now costs $11 to download, and HDDerase, a bootable DOS-based utility originally developed at the University of California San Diego’s Center for Memory and Recording Research, but which hasn’t been updated since 2008 and might not work with some drives or some configurations.The previously mentioned Ultimate Boot CD includes both HDDerase and the last free version of Parted Magic dating from 2013. Parted Magic is the better option because it has a graphical user interface for Secure Erase, but the last freely available version included in Ultimate Boot CD has some known issues that could brick drives and which have been resolved in later paid-only versions. The Linux hdparm utility can also be used to issue an ATA Secure Erase command, but is quite fiddly to use and comes with many warnings.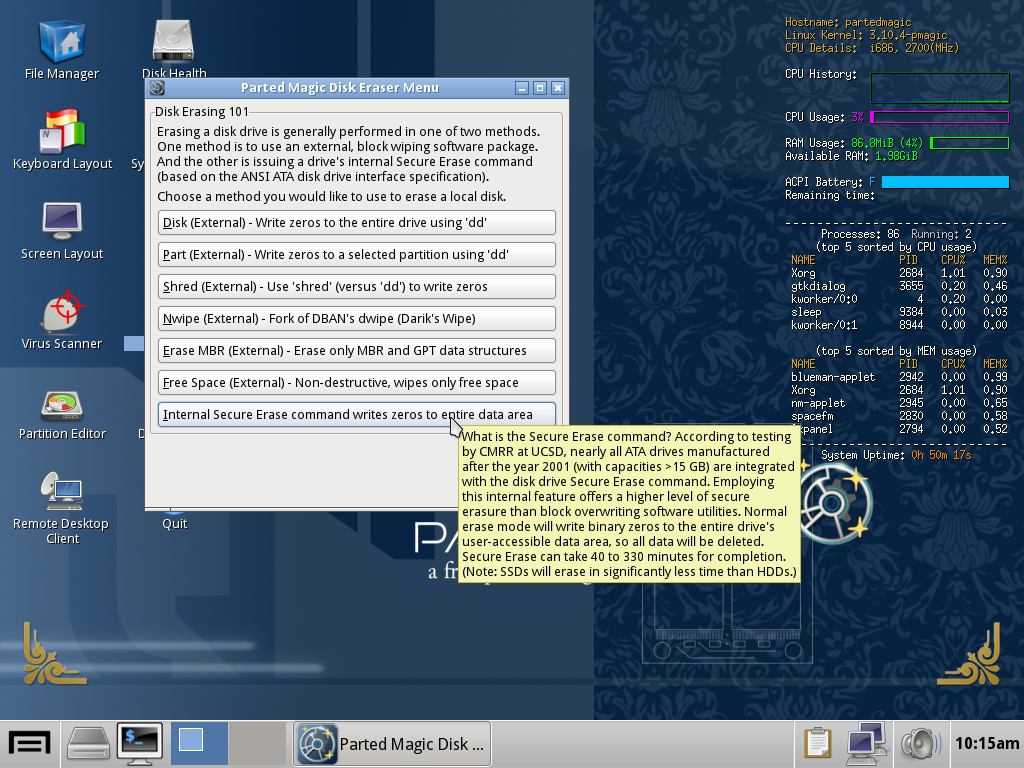 One important thing to keep in mind is that using the ATA Secure Erase command requires setting a user password for the target drive first. Choose something simple and easy to remember and never enter an empty password because certain BIOSes do not recognize NULL passwords and will no longer let you use that drive.It’s also not advisable to use Secure Erase on external drives that are connected to a computer over USB because USB-based interfaces might not support the command and there have been reports of bricked storage devices.Overwriting the entire SSD multiple times can be an alternative to Secure Erase, but such an operation can take many hours and even days to complete, depending on the drive's size, and is not always reliable. There's also a risk of drive failure due to the intensive workload.MacOSThe secure erase options offered for HDDs by macOS’ Disk Utility are not available for SSDs. Apple says in its documentation that these options “are not needed for an SSD drive because a standard erase makes it difficult to recover data from an SSD."However, difficult doesn't mean impossible, which is why the company also recommends turning on FileVault encryption when you start using your SSD drive for better security.
One important thing to keep in mind is that using the ATA Secure Erase command requires setting a user password for the target drive first. Choose something simple and easy to remember and never enter an empty password because certain BIOSes do not recognize NULL passwords and will no longer let you use that drive.It’s also not advisable to use Secure Erase on external drives that are connected to a computer over USB because USB-based interfaces might not support the command and there have been reports of bricked storage devices.Overwriting the entire SSD multiple times can be an alternative to Secure Erase, but such an operation can take many hours and even days to complete, depending on the drive's size, and is not always reliable. There's also a risk of drive failure due to the intensive workload.MacOSThe secure erase options offered for HDDs by macOS’ Disk Utility are not available for SSDs. Apple says in its documentation that these options “are not needed for an SSD drive because a standard erase makes it difficult to recover data from an SSD."However, difficult doesn't mean impossible, which is why the company also recommends turning on FileVault encryption when you start using your SSD drive for better security.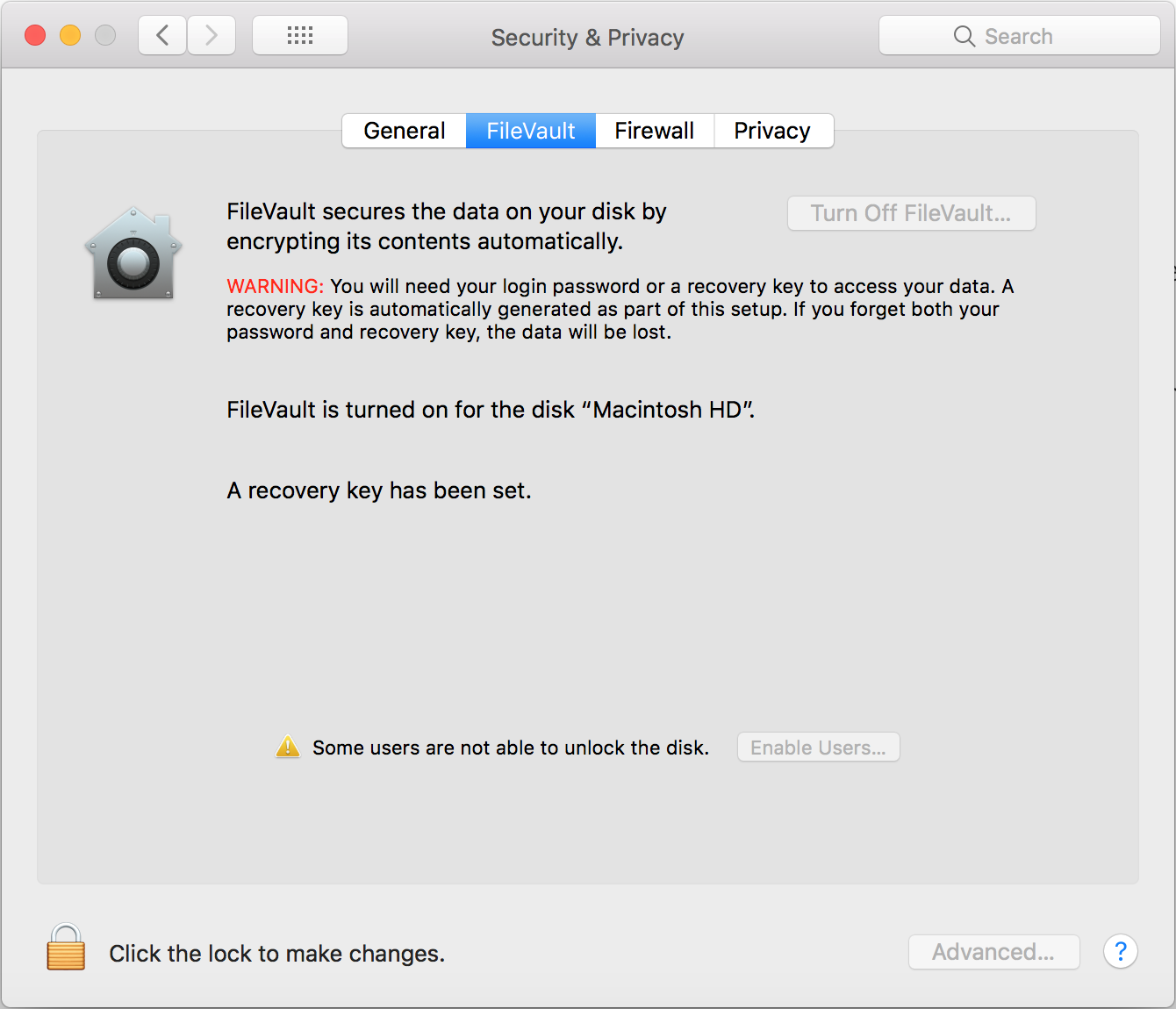 CaveatsUsing manufacturer-provided tools to perform data wiping, especially the Secure Erase command, is probably the safest choice because these companies supposedly know best how their products work internally. However, there have been documented failures in such tools over the years.In 2011, researchers from UC San Diego set out to study the effectiveness of common data sanitization techniques on SSDs and found serious issues with the implementation of the ATA Secure Erase command. Of 12 tested SSDs from different manufacturers, only eight supported the command and of those, only four executed it reliably.On two drives, attempts to execute the command returned an error and only the first block was deleted. Even more worryingly, one drive reported successful command execution without actually deleting any data at all.The study also found that fully overwriting SSDs twice was sufficient to sanitize most, but not all of them. For example, the researchers were able to recover 1GB of data, or around 1 percent, from one of the tested drives even after 20 overwrite passes by using specialized equipment attached directly to the drives’ memory chips.The per-file sanitization methods that typically work on HDDs and which involve overwriting a file's physical location on disk multiple times with random data proved completely inefficient on SSDs. The researchers were able to recover between 4 percent and 75 percent of the contents of files sanitized using such methods.Steven Swanson, the director of the Non-volatile Systems Laboratory at UC San Diego and one of the researchers behind the study, told me in an interview that he expects things to have improved since 2011, partly because their paper attracted a lot of attention at the time and put pressure on SSD makers to fix things. He believes that new SSDs from reputable manufacturers should have proper implementations of the Secure Erase command nowadays."If you're using a reputable piece of software to erase your SSD, I would trust it, if I was going to sell an SSD," he said.After an erase operation, a bootable live Linux environment can be used to check at a high level that the drive no longer has user data on it. Small pieces of information might still exist in the memory chips and wouldn’t be visible to such a test, but they wouldn't likely be of much use to a cybercriminal.Extracting that information in the first place would require specialized equipment that can read flash memory chips without relying on the SSD’s controller and this is not something that a random cybercriminal or a curious buyer would attempt doing.Another problem is that SSDs sometimes fail without warning, and not because their memory cells wear out, which is something that eventually happens to all flash-based storage over time. Different experts who have put SSDs through heavy testing have told me they've had cases where the drives suddenly stopped working and had to be thrown away."There are lots of other electrical components in there,” Swanson said. “The software that runs inside the SSD is very complicated and if it gets into a bad state, there's nothing really to be done and the SSD will just stop. That's a much more likely failure than flash chips going bad."Rutger Plak, a senior digital forensics expert at Dutch security firm Fox-IT, told me that he and his colleagues performed some non-academic data erasure tests on SSDs to see if they could be used internally for their work instead of HDDs—for example for collecting evidence from customer machines during digital forensics and incident response engagements. They ended up deciding against the idea because of reliability issues.The goal was to see if any data written to the drives could still be recovered after using the standardized multipass overwriting schemes that are commonly used to sanitize disks, Plak said. "A lot of SSDs broke when we tried to securely erase them or when we tried to write too much data too them."In some ways, things are simpler with mobile devices, even though they also use flash-based storage chips that have the same pitfalls as SSDs when it comes to data wiping.Recent versions of Android and iOS support full-device encryption, and many have it on by default, but this is a relatively new development and there are still a large number of phones in active use that are not encrypted, especially in the Android ecosystem.Android data wipingAndroid has a factory reset feature which formats the data partition that contains sensitive information and settings stored by applications and the OS. Phones that support removable microSD cards usually have a separate option for erasing and formatting the external storage.
CaveatsUsing manufacturer-provided tools to perform data wiping, especially the Secure Erase command, is probably the safest choice because these companies supposedly know best how their products work internally. However, there have been documented failures in such tools over the years.In 2011, researchers from UC San Diego set out to study the effectiveness of common data sanitization techniques on SSDs and found serious issues with the implementation of the ATA Secure Erase command. Of 12 tested SSDs from different manufacturers, only eight supported the command and of those, only four executed it reliably.On two drives, attempts to execute the command returned an error and only the first block was deleted. Even more worryingly, one drive reported successful command execution without actually deleting any data at all.The study also found that fully overwriting SSDs twice was sufficient to sanitize most, but not all of them. For example, the researchers were able to recover 1GB of data, or around 1 percent, from one of the tested drives even after 20 overwrite passes by using specialized equipment attached directly to the drives’ memory chips.The per-file sanitization methods that typically work on HDDs and which involve overwriting a file's physical location on disk multiple times with random data proved completely inefficient on SSDs. The researchers were able to recover between 4 percent and 75 percent of the contents of files sanitized using such methods.Steven Swanson, the director of the Non-volatile Systems Laboratory at UC San Diego and one of the researchers behind the study, told me in an interview that he expects things to have improved since 2011, partly because their paper attracted a lot of attention at the time and put pressure on SSD makers to fix things. He believes that new SSDs from reputable manufacturers should have proper implementations of the Secure Erase command nowadays."If you're using a reputable piece of software to erase your SSD, I would trust it, if I was going to sell an SSD," he said.After an erase operation, a bootable live Linux environment can be used to check at a high level that the drive no longer has user data on it. Small pieces of information might still exist in the memory chips and wouldn’t be visible to such a test, but they wouldn't likely be of much use to a cybercriminal.Extracting that information in the first place would require specialized equipment that can read flash memory chips without relying on the SSD’s controller and this is not something that a random cybercriminal or a curious buyer would attempt doing.Another problem is that SSDs sometimes fail without warning, and not because their memory cells wear out, which is something that eventually happens to all flash-based storage over time. Different experts who have put SSDs through heavy testing have told me they've had cases where the drives suddenly stopped working and had to be thrown away."There are lots of other electrical components in there,” Swanson said. “The software that runs inside the SSD is very complicated and if it gets into a bad state, there's nothing really to be done and the SSD will just stop. That's a much more likely failure than flash chips going bad."Rutger Plak, a senior digital forensics expert at Dutch security firm Fox-IT, told me that he and his colleagues performed some non-academic data erasure tests on SSDs to see if they could be used internally for their work instead of HDDs—for example for collecting evidence from customer machines during digital forensics and incident response engagements. They ended up deciding against the idea because of reliability issues.The goal was to see if any data written to the drives could still be recovered after using the standardized multipass overwriting schemes that are commonly used to sanitize disks, Plak said. "A lot of SSDs broke when we tried to securely erase them or when we tried to write too much data too them."In some ways, things are simpler with mobile devices, even though they also use flash-based storage chips that have the same pitfalls as SSDs when it comes to data wiping.Recent versions of Android and iOS support full-device encryption, and many have it on by default, but this is a relatively new development and there are still a large number of phones in active use that are not encrypted, especially in the Android ecosystem.Android data wipingAndroid has a factory reset feature which formats the data partition that contains sensitive information and settings stored by applications and the OS. Phones that support removable microSD cards usually have a separate option for erasing and formatting the external storage.
 Securely wiping data from older Android devices that don't support full-disk encryption is problematic, as shown in a 2015 study by researchers from the University of Cambridge. The researchers analyzed the efficiency of the factory reset implementation in 21 second-hand phones running Android versions between 2.3 and 4.3 and found that they could recover emails, text messages, Google access tokens and other sensitive data.Basic full-disk encryption was added in Android 4.4 and the feature was further improved in Android 5.0. However, turning it on by default was not mandatory for Android device makers until Android 6.0 and even then the requirement only applied to new devices that shipped with that OS version and not for older ones that received it though a software update.Low-end devices that don't support Advanced Encryption Standard (AES) performance above 50MiB/sec were exempted from the requirement and those exemptions still apply today for Android 8.1. According to the latest official statistics, only around 68 percent of Android devices that accessed the Google Play store over a 7-day period in late July were running Android 6.0 or newer.Fox-IT’s Rutger Plak told me that his company received many reports over the years from people who performed a factory reset on their Android devices then sold them and had their sensitive information stolen.If an Android phone that doesn’t use encryption gets factory reset and you can access its storage chip or card, then recovering data is very easy, Plak said. "There's a lot of software online for data recovery that is simply point-and-click and is very useful for recovering accidentally deleted files. However, if we think about it in terms of unsuspecting device sellers, then it's quite scary.""I'm afraid that if you have an old Android phone, my advice would be not to sell it," Ross Anderson, a professor of security engineering at the University of Cambridge Computer Laboratory, told me via email. "You really need to know what you're doing to wipe the data, as factory reset often doesn't work properly."Plak agreed that selling old Android devices is not a good idea and that using full-device encryption is the best way to prevent data recovery on newer devices. However, he also pointed out that it's very important to set a strong unlock passcode on the device, because the security of the data, even when encrypted, depends on that access code.iOS data wipingAs the sole maker of iOS devices, Apple has full control over the iOS ecosystem and does a good job of updating its users’ iPhones and iPads to the latest version of the OS.The company added full-device encryption in iOS 8 and it's turned on by default. Also, starting with the iPhone 5S, iOS devices have a security coprocessor called the Secure Enclave that handles cryptographic operations and stores the encryption key.This dedicated processor also prevents brute-force attacks against the phone's passcode by increasing input delays after each failed unlock attempt. That said, there are currently specialized devices marketed to law enforcement agencies that can reportedly crack 6-digit passcodes in up to three days, so users should strongly consider using longer alphanumeric codes.All iOS devices can be reset to factory settings by connecting them to a computer and using Apple’s iTunes software. Devices can also be erased without a computer from the Settings > General > Reset menu.If a mobile phone, hard drive or SSD contains data that's very sensitive, then it's probably best not to sell it. Storing it in a safe place from where it cannot be easily stolen or thoroughly destroying it so that data cannot be recovered are probably the best options.There are businesses that specialize in destroying storage devices and they will even provide a certificate of destruction, but their services are typically aimed at corporations and can be quite expensive.Destroying an HDD is relatively easy. Drilling holes or driving a few nails through its casing to damage the platters inside will usually be enough. Of course, safety gear should always be used when performing such operations.Drilling holes through platters, bending the platters or breaking the platters into multiple pieces are very successful HDD destruction methods, Gillware’s Nathan Little said."That's going to put the data unrecoverable by any commercial data recovery lab," Little's colleague Greg Andrzejewski said. "In theory, you might be able to read something back with some very specialized equipment, like a scanning electron microscope, but the way for-profit data recovery labs work is we attempt to repair that drive. […] So, we won't be able to recover anything from a drive that has the actual platters inside damaged to a certain extent."SSDs, on the other hand, have several memory chips and they all have to be destroyed in order to ensure that no data can be recovered. Typical 2.5" SATA SSDs have a protective case that needs to be removed in order to smash every chip, but SSDs that use the M.2 form factor have their chips exposed, so are easier to destroy.Despite appearances, phones require more work because their storage chips are integrated into their circuit boards and are well protected inside the compact devices. Getting to them will require disassembling the device, a process that's fiddly and different from one phone model to another.Modern phones are built to be pretty resilient so using fire to destroy them, as some people recommend on online forums, might not be such a great idea. First, you'd have to take them apart anyway to remove their built-in batteries because burning batteries is dangerous and carries a risk of explosion. Second, it will take a very hot and powerful fire to thoroughly damage a phone's internal components."We actually had a case where a phone was burnt with a body inside of a barrel and the phone was melted almost beyond recognition—you couldn't tell if it was a phone or a wallet," Little said. "It was just a shred of a phone and we were actually able to pull the chip on it and get a partial read and identify whose phone it was and get text messages and pictures off of it."An alternative to wiping data “is to physically destroy the device, smashing it up thoroughly so that the memory chip packages are broken into pieces," Ross Anderson told me. "Yet another alternative is to discard it in deep seawater, or bury it somewhere it won't be found."But smashing a phone into little pieces using a hammer might not be easy if the phone has a metal casing. If you decide to do that it’s also advisable to remove the battery first, so you’ll likely have to open up the case anyway.
Securely wiping data from older Android devices that don't support full-disk encryption is problematic, as shown in a 2015 study by researchers from the University of Cambridge. The researchers analyzed the efficiency of the factory reset implementation in 21 second-hand phones running Android versions between 2.3 and 4.3 and found that they could recover emails, text messages, Google access tokens and other sensitive data.Basic full-disk encryption was added in Android 4.4 and the feature was further improved in Android 5.0. However, turning it on by default was not mandatory for Android device makers until Android 6.0 and even then the requirement only applied to new devices that shipped with that OS version and not for older ones that received it though a software update.Low-end devices that don't support Advanced Encryption Standard (AES) performance above 50MiB/sec were exempted from the requirement and those exemptions still apply today for Android 8.1. According to the latest official statistics, only around 68 percent of Android devices that accessed the Google Play store over a 7-day period in late July were running Android 6.0 or newer.Fox-IT’s Rutger Plak told me that his company received many reports over the years from people who performed a factory reset on their Android devices then sold them and had their sensitive information stolen.If an Android phone that doesn’t use encryption gets factory reset and you can access its storage chip or card, then recovering data is very easy, Plak said. "There's a lot of software online for data recovery that is simply point-and-click and is very useful for recovering accidentally deleted files. However, if we think about it in terms of unsuspecting device sellers, then it's quite scary.""I'm afraid that if you have an old Android phone, my advice would be not to sell it," Ross Anderson, a professor of security engineering at the University of Cambridge Computer Laboratory, told me via email. "You really need to know what you're doing to wipe the data, as factory reset often doesn't work properly."Plak agreed that selling old Android devices is not a good idea and that using full-device encryption is the best way to prevent data recovery on newer devices. However, he also pointed out that it's very important to set a strong unlock passcode on the device, because the security of the data, even when encrypted, depends on that access code.iOS data wipingAs the sole maker of iOS devices, Apple has full control over the iOS ecosystem and does a good job of updating its users’ iPhones and iPads to the latest version of the OS.The company added full-device encryption in iOS 8 and it's turned on by default. Also, starting with the iPhone 5S, iOS devices have a security coprocessor called the Secure Enclave that handles cryptographic operations and stores the encryption key.This dedicated processor also prevents brute-force attacks against the phone's passcode by increasing input delays after each failed unlock attempt. That said, there are currently specialized devices marketed to law enforcement agencies that can reportedly crack 6-digit passcodes in up to three days, so users should strongly consider using longer alphanumeric codes.All iOS devices can be reset to factory settings by connecting them to a computer and using Apple’s iTunes software. Devices can also be erased without a computer from the Settings > General > Reset menu.If a mobile phone, hard drive or SSD contains data that's very sensitive, then it's probably best not to sell it. Storing it in a safe place from where it cannot be easily stolen or thoroughly destroying it so that data cannot be recovered are probably the best options.There are businesses that specialize in destroying storage devices and they will even provide a certificate of destruction, but their services are typically aimed at corporations and can be quite expensive.Destroying an HDD is relatively easy. Drilling holes or driving a few nails through its casing to damage the platters inside will usually be enough. Of course, safety gear should always be used when performing such operations.Drilling holes through platters, bending the platters or breaking the platters into multiple pieces are very successful HDD destruction methods, Gillware’s Nathan Little said."That's going to put the data unrecoverable by any commercial data recovery lab," Little's colleague Greg Andrzejewski said. "In theory, you might be able to read something back with some very specialized equipment, like a scanning electron microscope, but the way for-profit data recovery labs work is we attempt to repair that drive. […] So, we won't be able to recover anything from a drive that has the actual platters inside damaged to a certain extent."SSDs, on the other hand, have several memory chips and they all have to be destroyed in order to ensure that no data can be recovered. Typical 2.5" SATA SSDs have a protective case that needs to be removed in order to smash every chip, but SSDs that use the M.2 form factor have their chips exposed, so are easier to destroy.Despite appearances, phones require more work because their storage chips are integrated into their circuit boards and are well protected inside the compact devices. Getting to them will require disassembling the device, a process that's fiddly and different from one phone model to another.Modern phones are built to be pretty resilient so using fire to destroy them, as some people recommend on online forums, might not be such a great idea. First, you'd have to take them apart anyway to remove their built-in batteries because burning batteries is dangerous and carries a risk of explosion. Second, it will take a very hot and powerful fire to thoroughly damage a phone's internal components."We actually had a case where a phone was burnt with a body inside of a barrel and the phone was melted almost beyond recognition—you couldn't tell if it was a phone or a wallet," Little said. "It was just a shred of a phone and we were actually able to pull the chip on it and get a partial read and identify whose phone it was and get text messages and pictures off of it."An alternative to wiping data “is to physically destroy the device, smashing it up thoroughly so that the memory chip packages are broken into pieces," Ross Anderson told me. "Yet another alternative is to discard it in deep seawater, or bury it somewhere it won't be found."But smashing a phone into little pieces using a hammer might not be easy if the phone has a metal casing. If you decide to do that it’s also advisable to remove the battery first, so you’ll likely have to open up the case anyway.
The rapid development of technology has had a direct effect on the lifespan of consumer electronics in recent years. Device makers have an economic incentive to shorten product life cycles, but technology enthusiasts who want to have the latest and greatest gadgets also contribute to the trend.
Advertisement
What’s your threat model?
Advertisement
Encryption
Advertisement
Advertisement
Wiping hard disk drives
Advertisement
Advertisement
Advertisement
Solid-state drives (SSD)
Advertisement
Advertisement
Advertisement
Advertisement
Advertisement
Mobile devices
Advertisement
Advertisement
Advertisement
