This article includes both original reporting from Motherboard and reporting from The One Device: The Secret History of the iPhone.
The window shades are halfway down, leaving the bedroom dim. It's a grim day in Bassano del Grappa, a town in northeastern Italy that's mostly famous for its main import, the liquor of the same name: Grappa. I'm sitting on a twin bed—the only place I could sit. To my left, there's a bookshelf with a stack of Mickey Mouse comics, a staple in the childhood bedroom of every Italian kid. In front of me, sitting in a faux racing car chair, there's Luca Todesco, a 19-year-old who might be the best iPhone hacker on the planet.
The window shades are halfway down, leaving the bedroom dim. It's a grim day in Bassano del Grappa, a town in northeastern Italy that's mostly famous for its main import, the liquor of the same name: Grappa. I'm sitting on a twin bed—the only place I could sit. To my left, there's a bookshelf with a stack of Mickey Mouse comics, a staple in the childhood bedroom of every Italian kid. In front of me, sitting in a faux racing car chair, there's Luca Todesco, a 19-year-old who might be the best iPhone hacker on the planet.
Advertisement
I hand him my brand new, up-to-date iPhone 7."Can you jailbreak it?" I ask.Jailbreaking is the art of hacking into Apple's ultra-secure iOS operating system and unlocking it—and thus allowing users to customize the phone, and write or install any software unimpeded by Apple's restrictions. At the time I met with Todesco, in December 2016, there was no known jailbreak—no public knowledge of this hack—for the latest iOS version that was installed on my iPhone (iOS 10.2).The world's first jailbreaking step-by-step procedure, discovered in 2007, was posted online for all to see. Subsequent jailbreaks were used by millions of people. At one point, there was even a website—called jailbreakme.com—that was free for all to use and jailbroke your phone simply by visiting it.Todesco's jailbreak, however, is only available within the confines of his bedroom inside his parents house.
Luca Todesco jailbreaks an iPhone in his bedroom in Bassano del Grappa, Italy, in December of 2016. Photo: Lorenzo Franceschi-Bicchierai/Motherboard
Todesco, who is now 20 and is known by his hacker alias "qwertyoruiop," looks nonplussed. He grabs my phone and reaches for a cable on his desk, next to a collection of two dozen iPods and iPhones, all neatly resting next to each other as if on display. Todesco plugs in the phone, types a couple of commands into his Mac computer, then presses enter. My iPhone's screen turns off and on, before a white screen comes up:"Doing it … Patching … Jailbroken," the screen reads, one after the other."Ha!" Todesco says, smiling.
Advertisement
The wall of Apple's garden has been cracked. The phone is jailbroken.
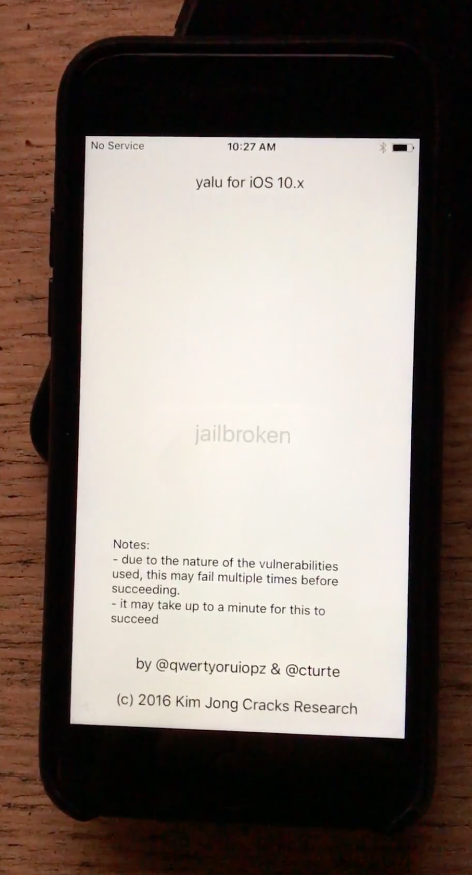
If it were the late 2000s, Todesco would probably post how he did that online, and would release his latest jailbreaking technique to the public. It'd then be available to all iPhone users, giving anyone a chance to unlock the phone and install apps not approved by Apple, or tweak the otherwise locked-in look, theme, and design of the phone's home screen.To jailbreak an iPhone means exploiting one or more bug to disable a security mechanism called code-signing enforcement. This allows the hacker to run code that's not signed and approved by Apple. By doing that, the hacker opens up the possibility to install apps not approved by Apple and make changes and tweaks to the operating system.Beginning shortly after the first iPhone was launched, and picking up steam in 2008, jailbreaking was a full-blown cultural and economic phenomenon. Hacking crews known by names such as the iPhone Dev Team, Chronic Dev, and evad3rs were some of the best iPhone hackers of their generation.They made both sport and crusade of breaking into Apple's ascendant phone and opening the system up to rogue developers. A brilliant, iconoclastic software engineer named Jay Freeman gave venue to the hackers and developers by building Cydia, a sort of alternative App Store. At its height, Cydia, which predated the actual App Store, was a business pulling in millions of dollars in revenue, and offered users a way to experience the iPhone as a truly free and open computer.
Advertisement
Things, however, have changed. The jailbreaking community is fractured, with many of its former members having joined private security firms or Apple itself. The few people still doing it privately are able to hold out for big payouts for finding iPhone vulnerabilities. And users themselves have stopped demanding jailbreaks, because Apple simply took jailbreakers' best ideas and implemented them into iOS.*When the iPhone 7 was released on September 16, 2016, Todesco found a way to jailbreak the new version of iOS within a few hours of getting his phone in the mail. He showed off his feat on YouTube, and told Motherboard he was able to do it so quickly because most of the bugs and exploits he needed for the jailbreak he had already found and developed for previous versions of iOS.Finding these bugs isn't easy. iOS is one of the—if not the—most secure and tough to hack operating system in the world. The code that underlies it is mostly secret. It's hard to figure out how anything works in iOS, let alone find flaws in it. Apple has always made security a priority in iOS, but the iPhone isn't unhackable. Anyone reading Apple's security notes after an iOS update will see a slew of bugs, some more serious than others. And there have been a few, albeit rare, cases of iOS malware, and a jailbreak created by government hackers with the goal of spying on victims was caught in the wild last year.
Advertisement
But it's undeniable that the iPhone is an almost-impervious walled garden, and only highly-skilled hackers or teams of hackers can penetrate it.While Todesco is happy to show that he can jailbreak the iPhone, both on YouTube and to Motherboard, the young hacker has no plans to release his secrets to the public. After all, his closely-guarded technique, and the bugs it relies on, are perhaps worth up to $1 million, according to market rates offered by zero-day merchants.The early pioneers of jailbreaking helped turn the original iPhone from a feature-light phone into a powerful tool that could do many of the things our phones do today, from playing video games to tracking your bike rides."In iPhone iOS 1.0, Apple didn't even have a fucking game, right? Every other phone had a copy of Snake, every phone had a copy of Hangman—[Apple] didn't even have Hangman," Freeman said, adding that the first iPhone couldn't even set ringtone profiles, or mute certain contacts at specific times of the day.
"These are features that you have on a phone, and these are features that the iPhone did not have," he said. "The iPhone came out and it was essentially a small tablet web browser that happened to sort of have a crappy phone wedged on it."Those were the Wild West days of jailbreaking, when talented, albeit amateur, hackers did it for fun, and to screw with Apple's walled garden."The iPhone came out and it was essentially a small tablet web browser that happened to sort of have a crappy phone wedged on it."
Advertisement
"It started as a group of teenagers writing NSA-grade exploits intended to spread software freedom," said a former Apple employee who asked to remain anonymous because he is bound by a non-disclosure agreement.For a while, the hackers spread freedom. And they gave people across the world the chance to mod their iPhone to enhance its capabilities."There was just so much fun stuff you could do—everyone jailbroke. iPhone OS 2 people still jailbroke because people wanted themes, people wanted copy-paste," Freeman, who is now 35, says. "There was so much basic low hanging fruit of what everyone expects a computer or phone to have that was easy to really make all those killer things."Ten years after the iPhone hit the sleek tables of Apple Stores worldwide, and the first-ever jailbreak, that Wild West is gone. There's now a professionalized, multi-million dollar industry of iPhone security research. It's a world where jailbreaking itself—at least jailbreaking as we've come to know it—might be over.*A skinny 17-year-old with unkempt curly hair and a slightly oversized button-up shirt stands awkwardly in what looks like his parents' kitchen, when he whips out an iPhone—the original one—from his jeans pocket."Hi everyone, this is geohot. And this is the world's first unlocked iPhone," George Hotz announced in a YouTube video that was uploaded in August of 2007.Working with a team of online hackers intent on freeing the iPhone from its AT&T bondage, Hotz logged 500 hours investigating the phone's weaknesses before finding a roadmap to the Holy Grail: First, he used an eyeglass screwdriver and a guitar pick to remove the phone's back cover. He found the baseband processor, the chip that locked the phone onto AT&T networks. Then, he overrode that chip by soldering a wire to it and running enough voltage through it to scramble its code. Pwned. On his PC, he wrote a program that enabled the iPhone to work on any wireless carrier.
Advertisement
Hotz filmed the result—a newfound ability to place calls with an iPhone using a T-Mobile SIM card—and shot to fame. A wealthy entrepreneur traded him a sports car for the unlocked phone. Apple's stock price rose on the day the news broke, and analysts attributed it to the fact that word was spreading that there was a way to get the "Jesus phone" without AT&T.The video has since been viewed over two million times.Though it wasn't technically a jailbreak, Hotz showed that there was appetite to hack the iPhone. So while Hotz worked to free the iPhone from AT&T's grip, a group of hackers had organized to break into the iPhone's walled garden. The hackers called themselves the "iPhone Dev Team." (The group had no affiliation with any actual development team at Apple, which has caused years of confusion.)"Back in 2007, I was in college, and I didn't have a lot of money," says David Wang, one of the members of the iPhone Dev Team.As a gearhead, Wang was intrigued when the iPhone was announced. "I thought it was a really impressive, important milestone for a device. I really wanted it," Wang remembers. "But the iPhone was too expensive for me, and you had to buy it with AT&T. But they also announced the iPod Touch, and I was like, I can afford that. I thought, you know, I could buy an iPod Touch, and they'll eventually release a capability to let it make web calls, right?"Or, he could just try to hack it into one.
Advertisement
"At the time, there was no App Store, there was no third party apps at all," Wang says. "I was hearing stuff about people who were modding it, the iPhone Dev Team, and the hackers, and how they got code execution on the iPhone. I was waiting for them to do the same with iPod Touch."The iPhone Dev Team was perhaps the most prominent hacker collective to take aim at the iPhone. They started probing the phone for code vulnerabilities—bugs that they would be able to exploit to take over the phone's operating system. Wang was watching, and waiting."Every product starts out in an unknown state," the cybersecurity expert Dan Guido says. Guido is the co-founder of the cybersecurity firm Trail of Bits, and an expert in iPhone security. Apple, he says, "lacked a lot of exploit mitigations, they had lots of bugs in really critical services."But that was to be expected. It was a new device, a new frontier. There were going to be potholes.It only took hackers a day or two to break into the iPhone's software after Chris Wade, now CTO at at 4Sense, found a way to exploit a bug that made Safari crash if you visited a website displaying a specially crafted TIFF image file. (The original TIFF bug was found by Tavis Ormandy, who now works for the elite hacking group Google Project Zero.) Hackers would post proof of pwning the system—uploading a video of a phone with an unauthorized ringtone, for example—and then typically follow-up with a how-to instruction set so other hackers could replicate it.
Advertisement
"When [the iPhone] came out, it was just for Mac," Wang says. "I didn't want to wait for people to come up with Windows instructions, so I figured out how they were doing it, and made a set of instructions for Windows users […] it turned out to be 74 steps."
That was a turning point. Wang, who goes by the handle planetbeing, posted his instructions online a few weeks after geohot's famous video, and it set off a frenzy. "So if you Google '74-step jailbreak,' you would see my name," Wang says. "It was the first thing that I did."That's how jailbreaking became the popular term for knocking down the iPhone's security system, and allowing users to treat the device as an actual computer—modifying settings, installing new apps, etc.Shortly after, Wang saw a blog post by the security expert HD Moore, who'd taken apart, step-by-step, that TIFF exploit. Moore had, in essence, laid out a blueprint for an automatic jailbreak.Wang wrote the predecessor to what would later become perhaps the most legendary—and trivial to implement—iPhone jailbreak mechanism. Instead of 74 steps, this jailbreak only required visiting an online "app" through Safari, a website called JailbreakMe.com, that would immediately jailbreak the phone.The first JailbreakMe, also known at the time as "AppSnapp," was released in October 2007, and soon became the stuff of legend."Every product starts out in an unknown state."
Advertisement
"The JailbreakMe attack … was really fun because at the time you could go into an Apple Store, open up JailBreakMe.com, and then it had this little 'Swipe to Unlock' button, and when you swipe to unlock it would run the exploit and root the phone from the internet," Guido says. "You could just go to an Apple Store and jailbreak every single phone they had on display."The Swipe to Unlock was a play on the iPhone's famous unlocking mechanic; a double entendre highlighting the fact that it was a closed, locked system that the dev team was liberating you from. Apple became so concerned about this practice that it later blocked the site JailbreakMe.com from its in-store Wi-Fi networks.
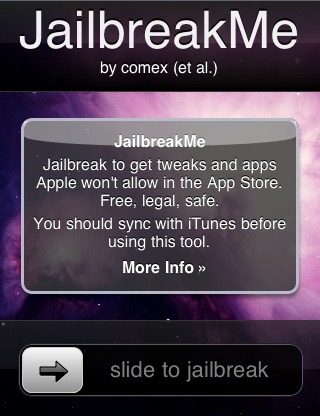
Apple, long aware that jailbreaking was becoming an increasingly mainstream trend, broke its silence on the practice on September 24, 2007, when the company issued a statement: "Apple has discovered that many of the unauthorized iPhone unlocking programs available on the Internet cause irreparable damage to the iPhone's software, which will likely result in the modified iPhone becoming permanently inoperable when a future Apple-supplied iPhone software update is installed."There were genuine reasons that Apple was concerned about jailbreaking. Guido says the JailbreakMe episode was "really funny, and really fun to do, but it's also tremendously demonstrative of how it's so easy to pull off that attack." The "star exploit," as it was technically called, Guido adds, "could have been turned around really quickly into an attack toolkit and we're lucky that it wasn't."
Advertisement
Or was it?Jailbreaks could in theory lead to people effectively exposing their devices to malware. Just last year, Chinese hackers stole hundreds of thousands of passwords from jailbroken phones.There's never been any evidence that a public jailbreak or an exploit used for one was recycled by malicious hackers to attack iPhones. Yet, after the hacker Nicholas Allegra, also known as Comex, released one of the versions of his famed JailbreakMe app, hackers repurposed it, swapping the payload to hack the users, according to two people who used to work for Apple."It seemed pretty rudimentary. It was just somebody swapping out the last part, everything else was identical," one of the sources, who asked to remain anonymous due to Apple's non-disclosure agreement, told Motherboard. "They swapped out the last part of the payload, so rather than launching Cydia at the end of the jailbreak process, they launched something else that they had cobbled together."
Unlike those unknown malicious hackers, the vast majority of the jailbreakers, like Wang, did it for the sport of it, and because they were eager to expand the capabilities of a clearly capable machine. The majority weren't hacking into anyone's phones (besides Apple Store display models, an easily reversible prank) and were only jailbreaking their own to customize them."People will try to break in, and it's our job to stop them breaking in."
Advertisement
Apple patched the bug that enabled the TIFF exploit, setting off what would be a years-long battle: The iPhone Dev Team and other jailbreaking crews would find a new vulnerability and release new jailbreaks. The first to find a new one would get cred. Then Apple would fix the bug, and "brick" the jailbroken phones, making them completely unusable. When asked about jailbreaking at a press event in September 2007, Steve Jobs called it "a cat and mouse game" between Apple and the hackers."I'm not sure if we are the cat or the mouse," Jobs admitted. "People will try to break in, and it's our job to stop them breaking in."Over time, the jailbreaking community grew in size and stature. The iPhone Dev Team reverse-engineered the phone's operating system to allow it to run third-party apps. Hacker-developers made games, voice apps, and tools to change the look of the phone's interface. On Apple's phone, you could customize very little. The original iPhone didn't even have an option for wallpaper, as the apps just hovered on a black background. And the fonts, layout, and animations were all set in stone. It was the hackers who were pushing the device to become more like the creativity augmenter, the knowledge manipulator that Steve Jobs's idol Alan Kay originally imagined mobile computing to be.
At its launch in February 2008, Freeman's Cydia allowed users to do a lot more than the current App Store does. Users could download apps, games, and programs, sure. But they could also download "tweaks" and more drastic overhauls. You could, for instance, redesign the layout of your home screen, download ad-blockers, apps to make non-AT&T calls, and exert more control over data storage.
Advertisement
Apple wasn't happy about it, and tried to discourage people from jailbreaking any way it could. In 2009, citing copyright law, Apple declared jailbreaking illegal. And though Apple never actually sued any of the jailbreakers, the practice remained in a legal gray area. A year later, the practice was ruled legal by the Librarian of Congress, clearing the way for more jailbreaks.Around this time, Allegra, another iPhone Dev Team member who was then 18, took over JailbreakMe, helping millions of people jailbreak their iPhones and install Cydia.The cat-and-mouse game between jailbreakers and Apple rolled on.The popularity of jailbreaking and Cydia provided a public demonstration of a palpable demand for a way to get new apps and for people to take control of their devices.Freeman saw it as more of an ideological imperative."The whole point is to fight against the corporate overlord," he told The Washington Post in 2011. "This is a grassroots movement, and that's what makes Cydia so interesting. Apple is this ivory tower, a controlled experience, and the thing that really brought people into jailbreaking is that it makes the experience theirs."As of 2011, Freeman said that his platform had 4.5 million weekly users, and was generating $250,000 in revenue a year, most of which was pumped back into supporting the ecosystem.Money was an issue for the jailbreakers like the iPhone Dev Team, who relied on PayPal donations and outside jobs to fund their efforts, Wang says. Over time, as the App Store drained some of the interest in jailbreaking, and Apple became increasingly aggressive in its efforts to prevent and discourage breaks, the original team began to drift off.
Advertisement
And it turned out that, as with any good underground rebels-versus-authority story, there was a twist: Evidence suggests, and a member of the the team confirmed, that one of the core iPhone Dev Team members was an actual Apple employee. None of the dev team had any clue that the hacker, who went by bushing and was known for his skills with reverse engineering, had been a double agent working for the company whose phones they were hacking. Who was he?Ben Byer had signed on as a Senior Embedded Security Engineer with Apple in 2006. At least, that's what his online trail suggests. A LinkedIn profile for Ben B. lists that same job title, as well as a work history that includes a stint with libsecondlife, an effort to create an open-source version of the once-popular Second Life game, where someone named "bushing" was a frequent poster. This would seem to suggest Byer was Bushing, which Wang confirmed to us. A person who used to work at Apple with Byer also confirmed that he worked there."We didn't know it at the time," Wang stammers today, reluctant to admit Byer's role in the iPhone jailbreaks. "We didn't realize until later. We didn't know it at the time, but he kind of came out to us later on." Bushing would go on to be a formidable force in the community. Tragically, he died in early 2016 due to what his friends and peers describe as natural causes. He was 36.The community's relationship with Apple wasn't always adversarial. The jailbreakers would sometimes drop by Apple's annual Worldwide Developers Conference and say hello to the security team. At one point, a hacker even left a hidden message to Apple's security team within one of his jailbreaks, naming specific engineers, according to the former Apple employee.
Advertisement
"A lot of the players were young folks with a lot of time on their hands and then they needed to get a job or graduated or whatever," a former Apple employee, who requested anonymity, told Motherboard. It was done "for fun," and "for the challenge," and "for the camaraderie.""There was a jailbreak community then," the former employee said.Years after the iPhone Dev Team gathered in IRC chat rooms, the public jailbreaks and YouTube shenanigans have slowly become a distant memory. One of the reasons was that the iPhone, in part because of the jailbreakers, has became harder to hack. Another reason is that the highly-skilled hackers who jailbroke it started getting jobs, either at Apple or at private security companies.
Image: Che Saitta-Zelterman
*A decade after the first jailbreak, the legacy of those early hacks lives on.The jailbreaker crews demonstrated living, coded proof that there was immense demand for an App Store, and that people would be able to do great things with it. Through their somewhat illicit innovation, the jailbreakers showed that the iPhone could become a vibrant, diverse ecosystem for doing more than making calls, surfing the web, and increasing productivity. And they showed that developers would be willing to go to great lengths to participate on the platform.As such, the hacker iPhone Dev Team should get a share of at least some of the credit in Jobs's decision to let the real iPhone Dev Team open up the device to developers in 2008.
Advertisement
"I don't want to have too much hubris in our role. We didn't know how much Apple had planned before us," Wang says, or how much it mattered that they relentlessly hacked the iPhone until it opened up. "I want to say it does."But now that Apple has incorporated into iOS some of the best tweaks and features that were previously only available through a jailbreak, does anyone—the average iPhone user—really need to jailbreak their iPhones?Truth is, they don't.Not that they could actually do it, either. As of this week, there's no public jailbreak for the current version of iOS. The last public jailbreak is for iOS 9.3.3, which was released on July 18, 2016, according to a jailbreak tracking site. In the last few years, jailbreaks have become increasingly rare.The increased security measures Apple has taken haven't just made it harder to get a full jailbreak, which now requires a chain of hard-to-find bugs. It also made jailbreaks, and the bugs and exploits that underlie them, too valuable to give up for free—or even to give to Apple for thousands of dollars.Last year, Apple's head of security and jailbreak-killer-in-chief, Ivan Krstić, boasted about the strength of iOS's defenses, pointing to the fact that jailbreaks these days require "between five and ten distinct vulnerabilities in order to be able to defeat platform security mechanisms.""After a decade of its existence there has still not been a single piece of iOS malware affecting our users at scale," Krstić said during a talk at the WWDC in 2016. "Our users have been fantastically well protected for nearly 10 years."
Advertisement
In January of this year, Todesco announced that his jailbreaking career was done."PSA: I will stop all public iOS research after I drop that 10.2 thing. The idiocy of the jailbreak community is too much to handle for me," he tweeted, before clarifying that "by 'public research' I mostly meant 'public [jailbreaks].'"When we met with him in December of last year, Todesco complained about the toxic environment in the modern jailbreaking community, where people bombard hackers like him asking for jailbreaks. These nagging requests for a timeline—"wen eta jailbreak?"—on the next jailbreak have become sort of a meme.Things indeed have changed."I feel like jailbreak's basically dead at this point," Allegra said in a recent chat through iMessage.Allegra said that if there was anybody who was going to "revitalize" jailbreaking, it would have to be Todesco. When we told him the Italian hacker had announced he was giving up jailbreaking, he wrote: "Oh? Too bad."For Freeman, the father of Cydia, a man who's seen countless jailbreaks, it's basically all over. Back in the good old days, he says, jailbreaks would work for months. Now, when there are public jailbreaks, they get killed immediately."Apple has both upped priority on fixing jailbreaks but also we have moved so far up the stack that we're actually dangerous," he says.Once a jailbreak crusader, it's gotten to the point where Freeman no longer recommends that people jailbreak their phones. It's dangerous, due to the higher risk of getting hacked, and it's not even worth it anymore, he says in a recent phone call."What do you get in the end?" he asks. "It used to be that you got killer features that almost were the reason you owned the phone. And now you get a small minor modification.""That turns into, like, a death spiral, where when you get fewer people bothering to jailbreak you get fewer developers targeting interesting things, which means there's less reasons for people to jailbreak," he added. "Which means there's fewer people jailbreaking, which causes there to be less developers bothering to target it. And then you slowly die."This story was adapted from an excerpt of The One Device: The Secret History of the iPhone , with additional original reporting.Motherboard staff is exploring the cultural, political, and social influence of the iPhone for the 10th anniversary of its release. Follow along.Get six of our favorite Motherboard stories every day by signing up for our newsletter."I feel like jailbreak's basically dead at this point."
